Vulnerable BlackBerry Workspaces Server API
By Justin Cobbs on October 26, 2017

BlackBerry Workspaces Server is a system designed for system administrators to manage workspaces, devices, and users. A recent vulnerability with this service involves taking advantage of an Application Programming Interface (API) with the service. An API is a set of subroutine definitions, protocols, and tools for building application software in computer systems. Gotham Digital Services (GDS), a cybersecurity research company, disclosed two vulnerabilities with this service to the public on October 16 with the coordination of BlackBerry. There are two vulnerabilities with the API inside BlackBerry Workspaces that allow an attacker to submit an unauthenticated request to eventually allow remote code execution on the server. These vulnerabilities are tracked as CVE-2017-9368: Sensitive Information Disclosure, with a Common Vulnerability Scoring System version 3 (CVSSv3) of 4.3, and CVE-2017-9367: Directory Traversal, with a CVSSv3 of 8.1.
Secure and Vulnerable Versions
GDS originally disclosed the vulnerabilities to BlackBerry on May 10, 2017. BlackBerry requested GDS to keep the vulnerabilities between each other until they could patch the vulnerabilities. Eventually, BlackBerry released an advisory for system administrators using the Workspaces Server components that are affected by these vulnerabilities, which are:
- Appliance-X versions 1.11.2 and earlier
- vApp versions 5.6.0 to 5.6.6
- vApp versions 5.5.9 and earlier
The Workspaces Server components that are unaffected by these vulnerabilities are:
- Appliance-X version 1.12.0 and later
- Appliance-X versions on the 1.11 codeline: versions 1.11.3 and later
- vApp version 5.7.2 and later
- vApp versions on the 5.6 codeline: versions 5.6.7 and later
- vApp versions on the 5.5 codeline: versions 5.5.10 and later
Sensitive Information Disclosure
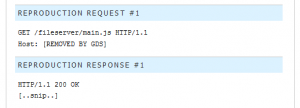
Eric Rafaloff, a researcher for GDS, discovered a vulnerability in BlackBerry Workspaces Server that allowed the source code for the application to be revealed. This involved sending an unauthenticated Hypertext Transfer Protocol (HTTP) GET web request to the file path: /fileserver/main.js. Although this is a simple vulnerability to be exploited, an attacker would need to have knowledge of the BlackBerry Workspaces Server file system format and have access to the network that the server is running on. Once the attacker has access to the source code, they could tailor their next attack based off of vulnerabilities with the code.
Directory Traversal
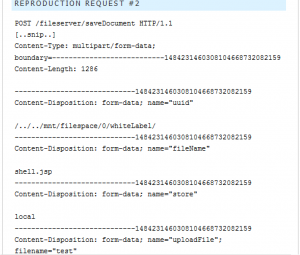
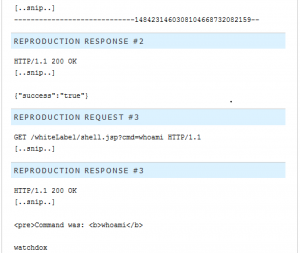
Using the returned source code of the application, Rafaloff discovered a directory traversal vulnerability that could be abused to upload files, such as a file containing code for a command prompt shell. This involved using a similar method as previously discussed in sensitive information disclosure, but to a different file path using a POST web request. Rafaloff found that the API, saveDocument, allowed unauthenticated file uploads to the web server. An attacker could exploit this vulnerability by sending a POST request to /fileserver/saveDocument to upload a file, such as shell.jsp, to /../../mnt/filespace/0/whiteLabel/. Once the file containing the shell code is uploaded, the attacker could then send commands to /whiteLabel/shell.jsp?cmd=(insert command here), through the GET web request to the web server.
Sources
BlackBerry Workspaces Services:
https://help.blackberry.com/en/blackberry-workspaces-administrators/current/
Server CVEs:
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9368
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9367
Vulnerability Write-ups:
http://support.blackberry.com/kb/articleDetail?articleNumber=000045696
http://www.securityweek.com/blackberry-patches-vulnerabilities-workspaces-server
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025