Intel Boot Guard Bypass
By Justin Cobbs on October 13, 2017
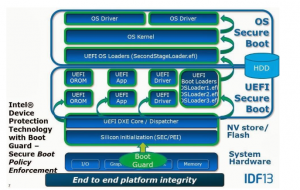
The Unified Extensible Firmware Interface (UEFI) and Basic Input/Output System (BIOS) are firmware interfaces that interact with the Operating System (OS) and computer firmware in modern computers. These features are used every time a computer system is powered on in order to start the hardware components and load the operating system from the hard drive. The well known Information Technology (IT) company, Intel, has their own implementation to protect the boot-up feature from been maliciously modified called Intel Boot Guard. Their product verifies the integrity of the BIOS by generating a cryptographically trusted boot chain using the Rivest Shamir Adelman (RSA) and Original Equiment Manufacturer (OEM) public keys. Although Intel Boot Guard is suppose to be secure, it has been proven to be bypassed on October 5 due to the proper configurations failing to be set by OEMs.
Attack Surface
 The boot guard bypass occurs with a process called BootGuardPei (GUID: B41956E1-7CA2-42DB-9562-168389F0F066), which verifies with Intel Boot Guard. After the verification process is completed, a Hand-Off Block (HOB) value gets stored as a zero, for failure, or a positive value, for success. The problem with the value is that a computer policy does not enforce the failure or success, so the BIOS moves on to running the Driver Execution Environment (DXE) for a integrity check via BootGuardDxe (GUID: 1DB43EC9-DF5F-4CF5-AAF0-0E85DB4E149A). If the integrity check fails, then the HOB returns an error – shutting the system down. An attacker could exploit this vulnerability by deleting the HOB to skip the DXE integrity check. They could also delete the entire section of code that verifies the integrity to bypass the check.
The boot guard bypass occurs with a process called BootGuardPei (GUID: B41956E1-7CA2-42DB-9562-168389F0F066), which verifies with Intel Boot Guard. After the verification process is completed, a Hand-Off Block (HOB) value gets stored as a zero, for failure, or a positive value, for success. The problem with the value is that a computer policy does not enforce the failure or success, so the BIOS moves on to running the Driver Execution Environment (DXE) for a integrity check via BootGuardDxe (GUID: 1DB43EC9-DF5F-4CF5-AAF0-0E85DB4E149A). If the integrity check fails, then the HOB returns an error – shutting the system down. An attacker could exploit this vulnerability by deleting the HOB to skip the DXE integrity check. They could also delete the entire section of code that verifies the integrity to bypass the check.
Steps to Bypass Boot Guard
Alex Matrosov, a security researcher who presented at Black Hat 2017, provided a step-by-step method for bypassing Intel’s Boot Guard. Matrosov specifies the following steps:
- Modify UEFI firmware update image with rootkit/implant or disable Intel Boot Guard
- Recalculate signature on 2048-bit RSA key pair for Initial Boot Block (IBB)
- Modify IBB manifest inside UEFI firmware update file
- Recalculate signature for IBB manifest with different 2048-bit RSA key pair
- Recalculate SHA256 hash of the public key from Root Key Manifest
- Modify Boot Guard configuration with active verified boot policy on the Management Engine (ME)
- Lock Boot Guard configuration with Field Program Fuses (FPF)
By doing so, an attacker could remotely modify an unsuspecting victim’s BIOS configurations to track and/or steal data without knowing that they have been made.
Vulnerable Models and Versions
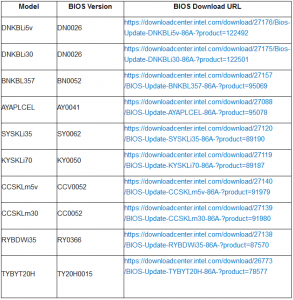
The Intel Boot Guard vulnerability is tracked as CVE-2017-5722 with a high vulnerability rating of 7.5. A security researcher for Embedi, Alexander Ermolov, specifies that multiple firmware based off of the AMI Aptio UEFI BIOS are vulnerable to be bypassed. The OEMs that utilize this type of BIOS are Dell, Gigabyte, ASRock, HP, Acer, Asus, and MSI. These companies own their specific motherboards, which have the vulnerable code that allows malicious users to bypass Intel’s Boot Guard. The product models and versions that are affected are listed on the picture to the left.
Available Patches
Intel has provided patches for multiple vulnerabilities related to their products that are suppose to protect the UEFI and BIOS on October 6. They have since then last updated these patches on October 10. The updates address the Intel Boot Guard Bypass vulnerability, as well as many other BIOS-related vulnerabilities. Other patches address Intel’s CVE-2017-5721: SMM Privilege Elevation, CVE-2017-5701: SPI Write Protection Bypass, and CVE-2017-5700: BIOS Administrator and User password bypass vulnerabilities.
Sources
Intel Boot BIOS Security Updates:
https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00084&languageid=en-fr
Boot Guard Analysis:
https://embedi.com/blog/bypassing-intel-boot-guard
https://github.com/REhints/BlackHat_2017/blob/master/Betraying%20the%20BIOS.pdf
BIOS CVE’s:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5722
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5721
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5701
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5700
Intel Boot Guard Article:
http://www.securityweek.com/flawed-bios-implementations-lead-intel-boot-guard-bypass