OnePlus Data Collection Practice/Apple ID Phishing
By Bryce Briggles on October 13, 2017
Earlier this week, security researcher Christopher Moore published a blog post detailing the questionable data collection practice of OnePlus. OnePlus is a smartphone manufacturer based in Shenzhen, China that runs OxygenOS, a custom version of the Android operating system.
The Shenzhen based company has been proven to be collecting user identification information in addition to the basic data most device manufacturers and software developers gather to improve the quality of their products.
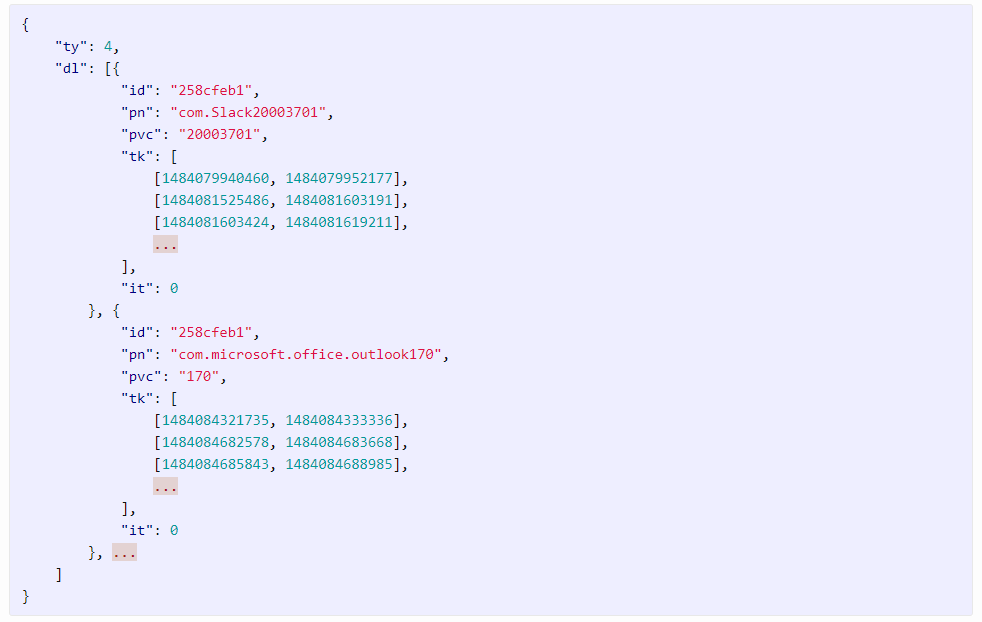
After intercepting the data his OnePlus phone sends to its servers, Moore discovered that the company was collecting:
- User’s phone number
- MAC addresses
- Device serial number
- Mobile network(s) names
- Wireless network ESSID and BSSID
- IMEI and IMSI code
- Time stamps when users lock and unlock their phone
- Time stamps when users open and close apps on their phone
- Time stamps when users complete activities in apps.
Moore contacted OnePlus support through Twitter about the situation, but was given no solution to the problem. Thankfully, an Android Developer named Jakub Czekanski provided a permanent fix to disable the data collection feature without having to root the device.
He stated on Twitter that a user can directly connect their OnePlus smartphone to a computer in USB debugging mode, open an adb shell, and enter: pm uninstall -k –user 0 net.oneplus.odm to permanently disable the data collection feature.
Apple ID Phishing
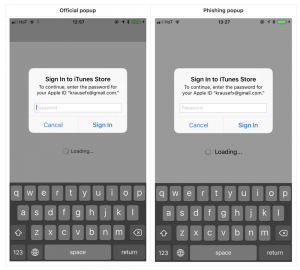
iOS Developer Felix Krause demonstrated a hard-to-detect phishing attack that can steal your Apple ID password. In his blog post published earlier this week, Krause showed how malicious apps can use UIAlertController to present fake alert messages to the user and steal their Apple ID password. iOS prompts users for their passwords all the time and that has led to people entering their passwords without thinking. Although he states that it is very easy to replicate Apple’s alert message, he claims there is no record of this kind of attack appearing in the wild.
You can circumvent this type of phishing by pressing the home button whenever a sign-in alert pops up. If the app closes and the alert remains, the message is legitimate. If both the app and the dialogue box close, then that was a phishing attempt.
It is also wise for users to never enter their credentials into a system pop-up unless they go directly to the source and to enable multi-factor authentication.
Sources:
https://thehackernews.com/2017/10/apple-id-password-hacking.html
https://thehackernews.com/2017/10/oneplus-oxygenos-analytics-data.html
https://www.chrisdcmoore.co.uk/post/oneplus-analytics/