Google search vulnerability allows forging of faulty Google search links
By Alfred Vergara on January 18, 2019
On January 7, 2019 cybersecurity professional Wietze Beukema reported a vulnerability in the Knowledge Graph of the Google search which allowed for the crafting of Google search uniform resource locators (URLs) with dubious results. This vulnerability allowed for a malicious person to create and send these false Google search URLs to other people as a type of misinformation.
Google Knowledge Graph
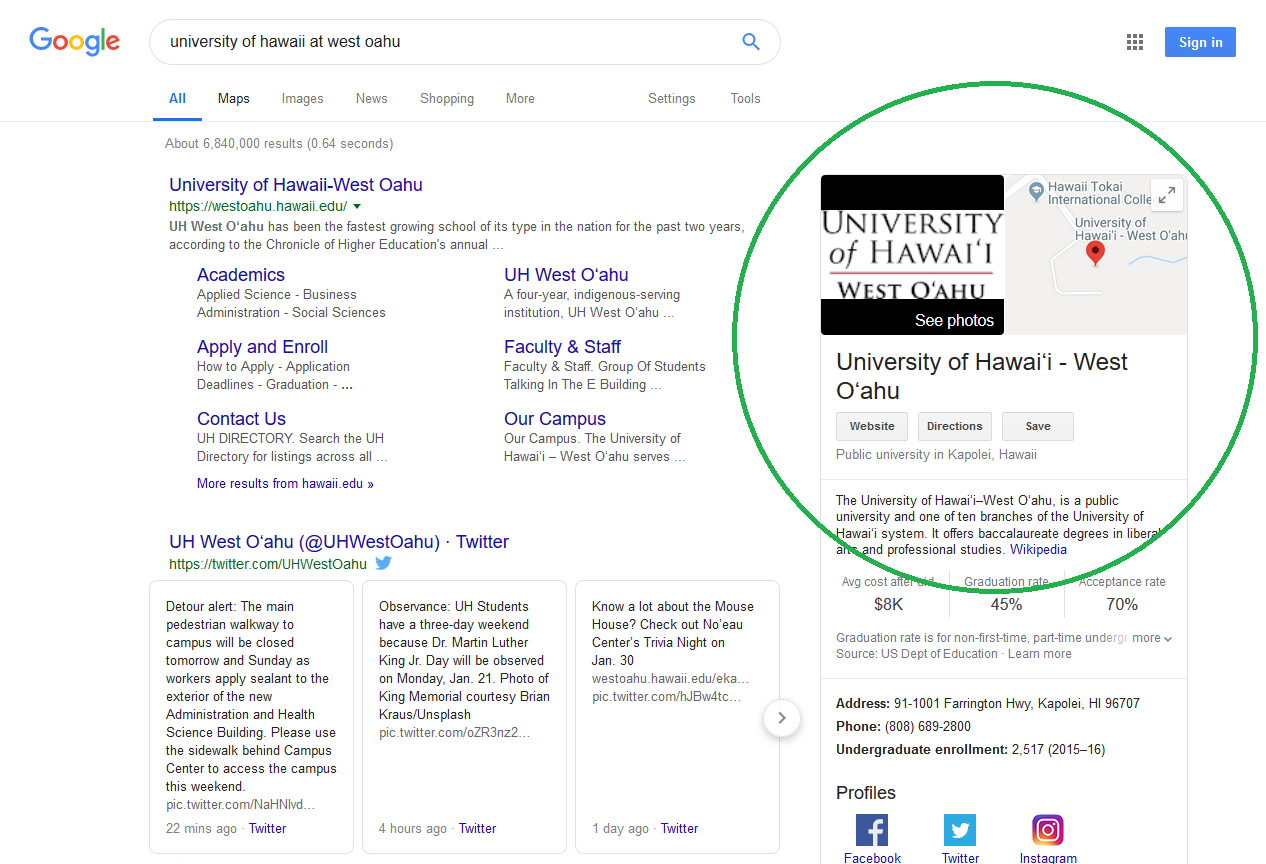
The Google Knowledge Graph was released as a feature of Google searches on May 16, 2012. Intended to make the search and research process easier, the knowledge graph provides a snippet of information about a search query with assumptions on the subject you want.
The Exploit
The Google Knowledge Graph and results of a search can be shared using the share button found on the Knowledge Graph. This link contains a different parameter than linking the Google search result URL itself: &kgmid, a parameter which references the knowledge graph that was given in this search. Beukema reported that this knowledge graph portion of the URL, the kgmid argument, could be appended to any Google search (kgmid=/m/03j24kf) and could change what is displayed in the Knowledge Graph. This meant that one could append any Knowledge Graph id (kgmid) into any search query to produce a different Knowledge Graph result. The Google search URL could be further modified with the &kponly parameter which in turn made the link to the Google search only display the Knowledge Graph. With both the &kponly parameter, and the addition of the kgmid parameter and identification number, a person could craft Google search URLs that displayed any result to any query.
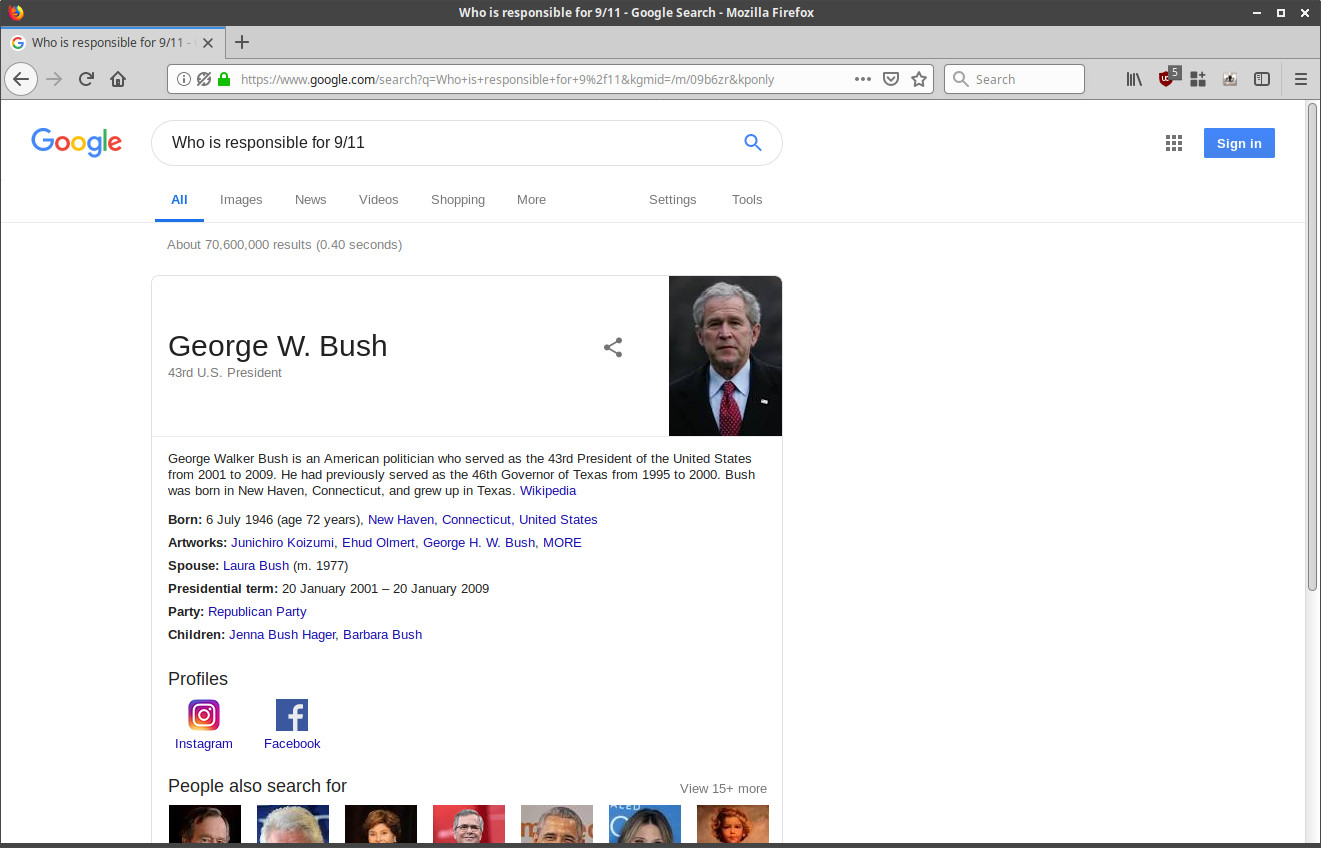
Significance
The handling of the Knowledge Graph parameter in URLs allowed for Google search results to be crafted to display any result. This has significance in a malicious person sharing faulty information. Misinformation, otherwise known as fake news, has been a topic of concern. Misinformation is only an issue when people do not conduct their own research and easily believe what is being reported as the truth. People are likely to trust a link with Google as the host. The exploit was very accessible in that it was not hard to create faulty search results. This meant that any person could advance their own agenda with “proof” to back it up.
Even more significant is that this exploit was detailed by Aaron Bradley in March of 2016. His report detailed similar information to that of Beukema, but without the &kponly parameter. It is possible that malicious persons could have found out about the &kponly parameter, and have been abusing the vulnerability since. The impact of knowing that Google search was exploitable in this way for so long is unmeasured, as both misinformation and its effects can be hard to detect.
Mitigation
Two days after the publication of Beukema’s article, Google patched the issue and disabled the kgmid parameter. Despite this, it is important to recognize that other search engines or online research bases can be compromised at any time.
Here are some steps you can take to prevent misinformation:
- Check other sources. In Google’s case, only the compromised links were affected. You could try other search engines to find information, or visit a library for research.
- Criticize information. Reports of any nature, news and research, cannot help but have some types of biases. Understand that the information may be flawed. Do not easily accept answers to questions unless verified by significant proof.
- Consult a professional. In the case of self-diagnosis of medical conditions through WebMD, seek a professional’s opinion on a topic to find the truth; don’t be afraid to seek a second opinion, or multiple professionals.
- Conduct your own research. In the case of researchers of any field, replicate the process of an experiment to verify results, and to verify the logical negation of a hypothesis.
Sources
Google Knowledge Base Vulnerability
https://plus.google.com/+AaronBradley/posts/92wjiusi2YC
https://www.wietzebeukema.nl/blog/spoofing-google-search-results
Google Knowledge Base
https://googleblog.blogspot.com/2012/05/introducing-knowledge-graph-things-not.html
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025