Memcached Server Attacks
By Robert Kuakini on March 2, 2018
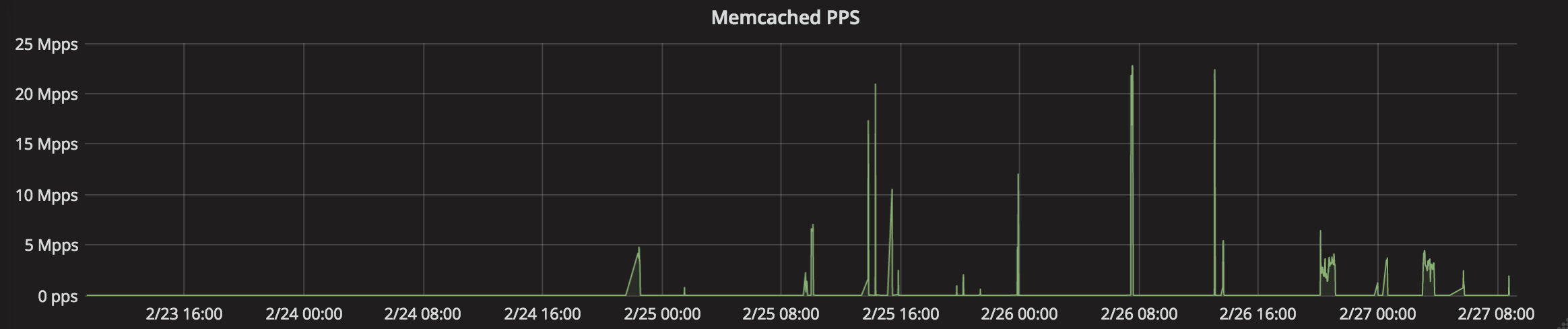
The past few days saw an increase in distributed denial of service(DDoS) attacks involving Memcached servers which were noticed by security researchers Cloudflare, Arbor Networks and Chinese internet security company Qihoo 360. They reported that the attacks had spiked between February 25th, and February 27th. Following this they released details about its attack vector, the type of attacks they are, and how to mitigate against them.
What is it?
Memcached is a “Free & open source, high-performance, distributed memory object caching system, generic in nature, but intended for use in speeding up dynamic web applications by alleviating database load”. According to Akamai, “This service is meant to cache data and reduce the strain caused by memory intensive services. Memcached can have both UDP and TCP listeners and requires no authentication”.
The DDoS attacks involving Memcached servers are a form of DDoS classified as a “DNS amplification attack”. According to CloudFlare, this attack “leverages the functionality of open DNS resolvers in order to overwhelm a target server or network with an amplified amount of traffic, rendering the server and its surrounding infrastructure inaccessible”. In this instance the attacks leveraged Memcached servers UDP to DDoS various targets.
Key Components
- Leverages misconfigured servers/UDP.
- DNS Reflection.
- DNS Amplification.
Servers/UDP
Memcached servers run the TCP or UDP port 11211. In this instance unprotected servers that have UDP enabled are being leveraged in the recent DDoS attacks. By using UDP there are no checks of the receiving data ensuring that majority of the data will be delivered. This is due to UDP not requiring a source address in its headers. Exposed Memcached servers not protected by a firewall are susceptible of being taken advantage of by attackers.
There a number of vulnerable Memcached servers around the world giving attackers lots of servers to leverage. Cloudflare notes that they have currently only seen “5,729 unique source IPs of memcached servers” and are expecting much more frequent and larger attacks in the future. Their Shodan reports 88,000 open Memcached servers as of February 26th, 2018.

DNS Reflection
A DNS amplification attack utilizes DNS reflection and amplification techniques to form a potent DDoS. The attacker spoofs an IP sending a request to a vulnerable UDP server, in this case it is a Memcached server. The DNS server then responds back not to the spoofed host but instead to the victim. These responses will begin to overwhelm the target draining resources and causing a denial of service.
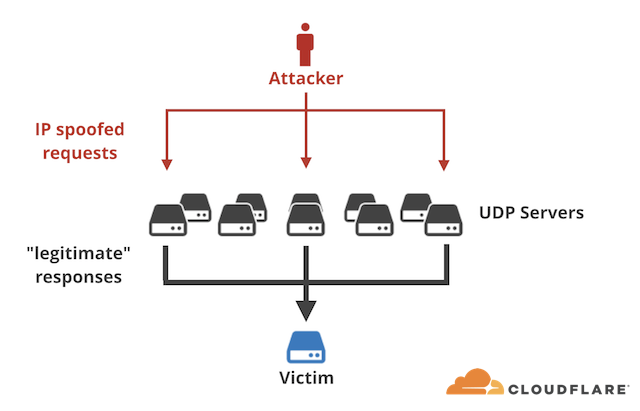
DNS Amplification
The second aspect of these attacks is DNS amplification. By utilizing vulnerabilities in misconfigured servers attackers are able to turn a small query into a larger one. A query could send a request that is 15 bytes in size but trigger a response containing 134KB. This is an example of only a single packet and from those monitoring these attacks have witnessed much higher amplification of packets. These requests can be sent in rapid succession snowballing into larges gigabyte response packets.
Mitigation
Cloudflare listed several things that should be taken to prevent Memcached servers from being used in DDoS attacks.
- Disable UDP if it is not in use.
- Firewall servers from the internet.
- Try not to develop using UDP and do not have it set to enabled by default.
- ISP’s need to fix vulnerable protocols and IP spoofing.
Significance
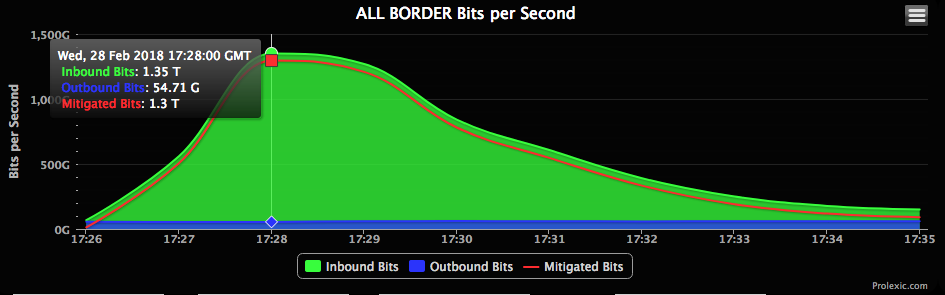
GitHub had suffered an attack on Wednesday February 28, 2018. It had suffered roughly 1.35 terabits per second of traffic making it the most powerful DDoS attack to date. Smaller attacks had occurred but these seem to be testing the attack vector or focused on smaller scale operations. GitHub is an example of how the attacks have the potential to launch some of the biggest DDoS attacks in their fields and with the amount of Memcached servers around the world and the recent spikes of DDoS related to them it should be noted that more will be coming in the future.
Conclusion
Like many DDoS attacks they will appear suddenly and effectively halt operations in a short period of time. Despite this, as users, developers, system administrators, and internet service providers become more aware of this issue, Memcached servers will be fixed to reduce this attack vector. Even though this is attack vector is powerful operational plans to handle and recover from them have become more effective at combating downtime and damages. With proper maintenance and proactive measures the effectiveness of these types of attacks can be greatly reduced. One example of this “Ofer Gayer, senior product manager at security firm Imperva, said many hosting providers have decided to filter port 11211 traffic to help blunt these memcached attacks.”
Sources:
Akamai, https://blogs.akamai.com/2018/02/memcached-udp-reflection-attacks.html
Cloudflare, https://blog.cloudflare.com/memcrashed-major-amplification-attacks-from-port-11211/
DDoS Mon, https://ddosmon.net/insight/
Hackaday, https://hackaday.com/2018/03/01/memcached-servers-abused-for-ddos-attacks/
Helpnet Security, https://www.helpnetsecurity.com/2018/02/28/memcached-based-reflected-ddos-attacks/
Krebs, https://krebsonsecurity.com/2018/03/powerful-new-ddos-method-adds-extortion/
Memcached, https://memcached.org/
Network World, https://www.networkworld.com/article/3258772/security/memcached-servers-can-be-hijacked-for-massive-ddos-attacks.html
Threat Post, https://threatpost.com/arbor-ddos-attacks-getting-bigger-as-reflection-increases/108752/
Threat Post, https://threatpost.com/large-scale-ddos-attacks-continue-to-spike/107254/
Threat Post, https://threatpost.com/misconfigured-memcached-servers-abused-to-amplify-ddos-attacks/130150/
Wired, https://www.wired.com/story/github-ddos-memcached/
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025