Jackpotting, The Wrong Type of Jackpot
By Robert Kuakini on February 2, 2018
Brians Krebs reported on the first known ATM jackpotting attacks to occur in the U.S. on January 30, 2018. The attacks were not a surprise, as the ATM vendor Diebold/Nixdorf released a security alert on January 25,2018 to their customers stating attacks that occurred in Mexico were moving to the United States. This alert contained a description of the attack, the type of terminals at risk, and recommendations for countermeasures. The full alert can be found here.

What is Jackpotting?
The concept of Jackpotting has been a global threat from at least 2010 with incidents being reported from Europe, Asia, and Latin America, with the U.S. now joining this list. According to Krebs,
ATM Jackpotting is a sophisticated crime in which thieves install malicious software and/or hardware at ATMs that forces the machines to spit out huge volumes of cash on demand.
The Attack Process
- Gain physical internal access to an ATM through the top-hat of the terminal.
- Use an endscope instrument to locate internal portion of the cash machine.
- Attach a cord that allows them to sync their device to the ATM’s computer.
- Use a keyboard or device to access the ATM’s computer.
- Install the ATM Malware.
- Activate Ploutus with an activation ID.
- Send a command to execute Ploutus to dispense cash.
- Collect cash with money mule.
This is a summarized attack process and is no way an absolute methodology to ATM attacking. The actual attacks will come down to individual criminals or groups, their tools, and the technology they will utilize.
Ploutus
FireEye released a research report written by Daniel Regalado on January 11, 2017 about the ATM malware used in these recent attacks. It is called Ploutus-D, a variant of the 2013 version Ploutus. The ATM malware interacts with KAL’s Kalignite multivendor ATM platform in order to dispense cash.
Features of Ploutus-D
Taken from the FireyEye report these are the unobserved features of Ploutus-D:
- It uses the Kalignite multivendor ATM Platform.
- It could run on ATMs running the Windows 10, Windows 8, Windows 7 and XP operating systems.
- It is configured to control Diebold ATMs.
- It has a different GUI interface.
- It comes with a Launcher that attempts to identify and kill security monitoring processes to avoid detection.
- It uses a stronger .NET obfuscator called Reactor.
Ploutus-D can run as a stand alone application or as a windows service started by a launcher.
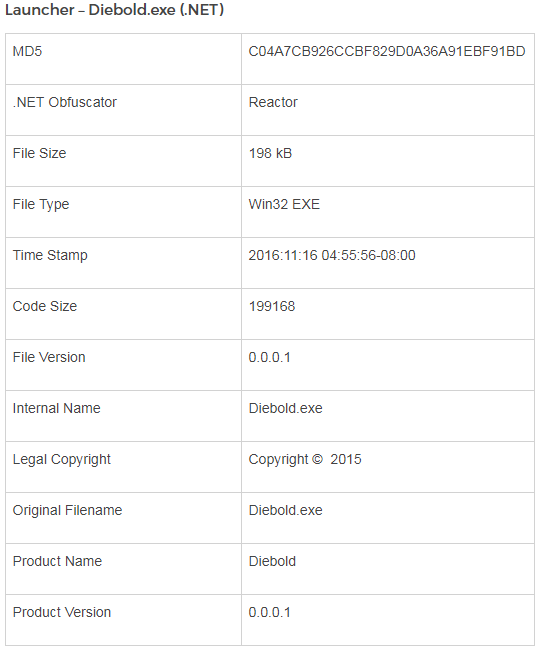
The launcher can then be interacted with by using a keyboard connected to the ATM.

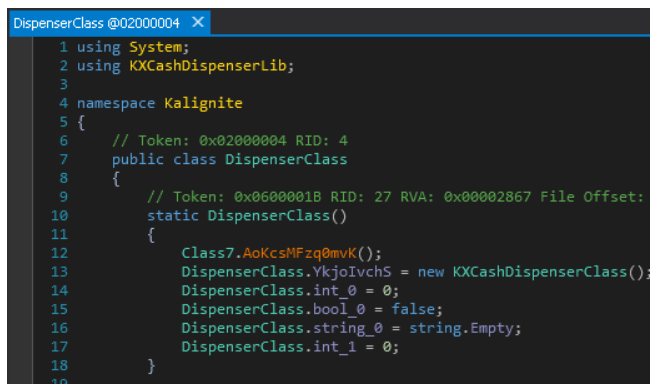
The “KXCashDispenserLib” uses the Kalignite Platform to interfact with the XFS manager to control the dispenser. This controls the dispenser that releases the money.
Demonstration
Jackpotting can be conducted in a number of ways. A 2010 Blackhat presentation by the late Barnaby Jack showcased “jackpotting” going into detail on methodologies, processes and tools used to exploit and hack several types of ATM’s. Below is a 40 minute recording of the Black presentation.
Targets
U.S. attacks have been a handful of older model cash machines from the ATM vendor Diebold Nixdorf. FireEye, noted that with minimal changes targets could be expanded to run “ runs on 40 different ATM vendors in 80 countries.” with the potential for financial loss to be extremely high.
Recommendation for Countermeasures
The Diebold/Nixdorf security alert recommended some some countermeasures.
- Limit physical access to the ATM.
- Locking mechanisms.
- Controlled areas to the ATM.
- Multi-factor authentication.
- Implement protection mechanisms for cash modules.
- Update to latest firmware.
- Setup or use encryption communications.
- Setup additional measurements.
- Monitor unexpected opening of top hat compartment.
- Keep operating system and software stack up to date.
Conclusion
As a consumer who uses ATM’s are you affected by jackpotting? No only, financial institutions and ATM vendors are directly affected by these attacks. However, you should still be concerned as these attacks show that ATM’s can be manipulated for criminal financial gain, demonstrating a lack of security on these machines that see daily usage. ATM’s come with a general expectation that they are secure and protected because we use them to withdraw our money from them. When criminals physically manipulate these machines for their own financial gain we tend to lose confidence in how our institutions can protect our money.
Research Materials:
https://www.fireeye.com/blog/threat-research/2017/01/new_ploutus_variant.html
Sources:
https://www.wired.com/2010/07/atms-jackpotted/
https://krebsonsecurity.com/2018/01/first-jackpotting-attacks-hit-u-s-atms/
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025