ICS Summary for Week of January 26th
By Nathaniel Weeks on January 26, 2018
Trisis (Triton) Overview
The Trisis Malware (also referred to as Triton and HatMan) is not a new piece of malware this week. It was discovered last August in a Saudi Arabian oil and gas plant. It targets Schneider Electric Triconex SIS systems (Triconex being where the malware gets its name). The attack was carried out by exploiting a zero-day vulnerability and then via a remote access trojan (RAT). Malware targeting safety instrumented systems (SIS) is a first and represents a new angle of attack on industrial control systems (ICS). The Python 2.7 code that the malware is written in is buggy but managed to shut down systems intermittently and eventually caused the plant to completely shut down. What is new this week in regards to this story, is a report from CyberScoop which states that the malware Trisis has been mistakenly released to the Internet.
The Trisis release:
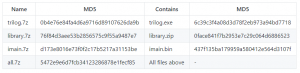
The malware was uploaded to VirusTotal by Schneider Electric per industry protocol. It was then picked up and distributed from there. The initial response to the disclosure was to take Trisis off VirusTotal for fear of malicious actors getting possession of the malware, but it was believed that malicious actors might already have access to the files. The files are back on the site for a different reason: research. Github is now hosting the files (repo: https://github.com/ICSrepo/TRISIS-TRITON-HATMAN) for the purpose of research and aiding administrators to identify the files if they make it onto their networks. The MD5s of several of the files are included.
There are also yara rules for identifying the files associated.
Significance:
Trisis has been referred to as “Stuxnet’s sibling” and represents only the fifth documented malware capable of causing physical damage to an ICS. This malware has the ability to shutdown critical infrastructure and is now freely available. According to Schneider, the vulnerability in the Tricon firmware “is limited to a small number of older versions of the Tricon”. It is believed that the attack (likely by a nation-state) was carried out on an unguarded piece of infrastructure. This is the reason for Schneider’s recommendation via their report: “Physical controls should be in place so that no unauthorized person would have access to
the safety controllers, peripheral safety equipment or the safety network”. Along with Schneider’s recommendation, if possible, update the firmware of the ICS and make sure antivirus software is up-to-date.
This malware is a continuation in the escalating threat to industrial control systems. Threats will continue, and while zero-days will persist, Trisis represents the need for best practices and vigilance.
Sources:
ICS US-CERT
https://ics-cert.us-cert.gov/sites/default/files/documents/MAR-17-352-01%20HatMan%E2%80%94Safety%20System%20Targeted%20Malware_S508C.pdf
Schneider Electric
https://www.schneider-electric.com/en/download/document/SEVD-2017-347-01/
SecurityWeek
http://www.securityweek.com/triton-malware-exploited-zero-day-schneider-electric-devices
Dragos White Paper
https://dragos.com/blog/trisis/TRISIS-01.pdf
https://github.com/ICSrepo/TRISIS-TRITON-HATMAN
CyberScoop
https://www.cyberscoop.com/trisis-virus-total-schneider-electric/