Skygofree “Are You Being Watched?”
By Robert Kuakini on January 19, 2018

Kaspersky Labs released a technical document on January 16th, 2018 regarding the discovery of a powerful Android spyware, Skygofree. Having been continuously developed since the end of 2014 its functionality and features have grown it into one of the most advanced surveillance tools around. A number of unique features distinguishes it, such as the ability to record and upload audio from the device, track a devices location and react based on this information, and create a new WiFi connection forcing the device to connect to it.
What is it?
Initially discovered in October 2017, Skygofree is one of Android’s most advanced spyware to date, specializing in surveillance equipped with powerful capabilities. It uses methods of a typical Trojan to download itself onto an Android device disguising itself as installing, then proceeds to hide in legitimate services awaiting instructions from a command and control (C&C) server. Depending on the context of the occasion and the needs of the server, it then exploits a number of known vulnerabilities within the Android OS to gain root privileges. Once it gains these privileges it can be instructed to use many of its surveillance features according to the instructions it receives.
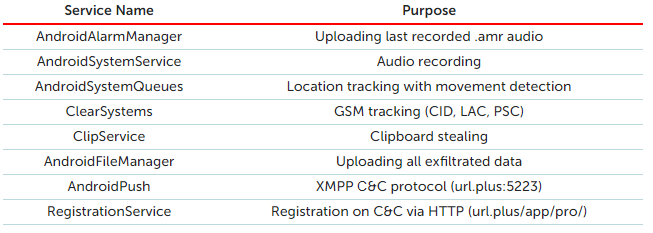
What does it do?
BleepingComputer’s Catalin Cimpanu, posted a summarized list of Skygofrees potential capabilities from Kaspersky’s in-depth technical analysis. It is recommended to go through this technical analysis as it provides much more detail on the Skygofrees features.

An initial glance shows how powerful Skygofree’s arsenal truly is. For example, it could be used for tracking political dissidents, locating a person of interest, exfiltrate sensitive data, blackmail, or other clandestine activities. The only thing limiting of what it could be used for is one’s imagination. All of this is made possible due to the flexibility of the payloads available.
Also contained in the list are the rooting exploits that the Skygofree payloads use. These exploits take advantage of vulnerabilities located within the Linux kernels by leveraging incorrect data/value checking, unrestricted or vulnerable system calls, and insufficient memory address protection.
How it is distributed
The method in which Skygofree is distributed is through fake mobile operator websites, where Skygofree is disguised as an update to improve mobile internet speed. Once downloaded it conceals itself from the user only displaying a “setup is in progress” notification while it waits for further instructions from the command server. Below are some of the landing pages used to distribute it, although many of the domains are outdated some are still active.
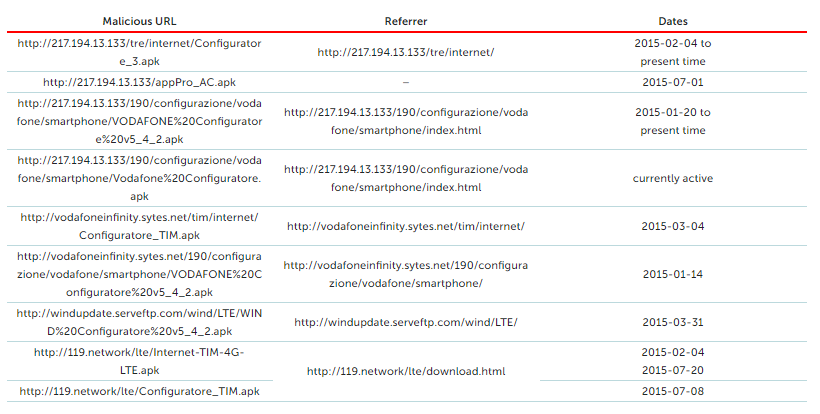
Best ways to protect yourself
While the vulnerabilities still exist Kaspersky recommends the best ways to protect yourself:
- Install apps only from official stores – Make sure you only download apps from official or trusted sources.
- Unsure about the app? – Don’t download, verify it can be trusted. Look for small details such as misspelled app names, small numbers of downloads, or dubious requests for permissions.
Should you be worried?
There are an estimated 2 million Android devices in the world. Many of which have the potential to become a mobile surveillance device for malicious purposes. Users could unknowingly be assisting hostile entities with their goals or potentially setting themselves up for blackmail. Sensitive information kept on the device, messages, surroundings or within earshot could be leaked without the user’s knowledge. Apple users while not directly vulnerable to Skygofree could be near an Android user who is.
So while the existence and capabilities of Skygofree are terrifying, to date there are only a few known occurrences all of which have been in Italy and only limited to Android devices. However, due to the nature of malware, the distribution methods could change and we may see Skygofree or a variant of it start appearing in other areas of the world or on Apple devices. By following best security practices will you be able to mitigate your chances of being infected.
CVES:
CVE-2013-2094
CVE-2013-2595
CVE-2013-6282
CVE-2014-3153
CVE-2015-3636
Sources:
https://thehackernews.com/2018/01/android-spying-malware.html
https://securelist.com/Skygofree-following-in-the-footsteps-of-hackingteam/83603/
https://www.kaspersky.com/blog/Skygofree-smart-trojan/20717/
https://arstechnica.com/information-technology/2018/01/found-new-android-malware-with-never-before-seen-spying-capabilities/
https://www.bleepingcomputer.com/news/security/italian-it-company-possibly-behind-new-Skygofree-android-spyware/
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025