Google “Buganizer” Bugs
By Justin Cobbs on November 9, 2017
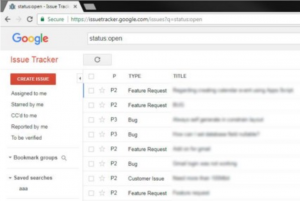
Google employees utilize an online tool called Google Issue Tracker, otherwise referred to as the Buganizer System by Google employees, to track every bug and potential new feature with product development. This tool is also utilized by partners outside of Google that collaborate with each other on certain projects and to public users who were given access to use the Issue Tracker with their project. Anyone with an @gmail.com email account can also open their own tickets to report bugs with Google tools or view a list of open tickets referring to current bugs and feature requests by typing in “Status: Open” on their website. However, Gmail account users are unable to see further details about the status of an opened ticket such as displaying the bugs and work being done to resolve the issue with a time estimate. On October 30, bug bounty hunter Alex Birsan posted an analysis of how he exploited Google’s Buganizer System that earned him around $16,000 in payouts from Google’s bug bounty program.
Obtaining an @google.com Address

In order to read further details on the progress of a bug resolution or new feature, a person would need to sign in with an email address with an @google.com email extension. The email format that would respond to the ticket tracking system would be set as buganizer-system+componentID+issueID@google.com. The componentID section of the email would specify the category that a bug or feature belongs to, such as the number representing the vulnerability reports section of bugs. The issueID section of the email would specify the thread that an employee or specially granted person is responding to. Any Gmail user should not be able to create a @google.com email address, but according to bug bounty hunter Alex Birsan, he was able to do so. Birsan was able to create a Google email by signing up for a regular @gmail.com email address, ignoring the confirmation email, changing his email address to an @google.com address, then clicking on the confirmation link sent by Google to confirm the creation of his newly created @google.com email address. Birsan submitted the details on this vulnerability to Google, which they accepted the vulnerability within 11 hours and awarded him $3,133.7.
Ticket Notification Vulnerability
An owner of an @gmail.com email extension has the ability to star the topics that are of interest to them to receive update notifications of the status of the ticket to their email. Birsan was able to confirm that an attacker could receive email notifications for the tickets that they modify the issueID of for a few thousand tickets, which would be forwarded to their Gmail account. Although an attacker could receive email notifications on ticket updates, they would only be able to receive notifications on the tickets relating to translating languages at the time of this writing. Regardless, Birsan submitted his report to Google, which they accepted within 5 hours and awarded him $5,000.
Sensitive Information Disclosure
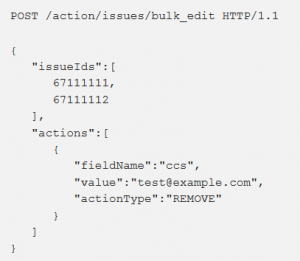
According to Birsan’s analysis, an attacker could retrieve the complete details regarding to any ticket in the database by specifying the issueIds’s section in a block of code he found in a Javascript file that was linked to an Application Programming Interface (API) of the application. The attacker could modify this section of code and sent it via an Hypertext Transfer Protocol (HTTP) web POST request. From this point on, an attacker could monitor the updates of tickets in the vulnerability reports section to exploit them before they are patched. Although this is considered a severe sensitive exposure of information, an attacker would have to spend a lot of time sifting through thousands of email notifications in order to find a vulnerability to exploit. Google also usually patches severe vulnerabilities within one hour, so this vulnerability is actually harder than it looks to successful take advantage of. Google accepted this vulnerability and disabled the feature within an hour of Birsan’s submission and awarded him $7,500.
Sources
Buganizer Analysis:
Google Issue Tracker:
https://developers.google.com/issue-tracker/
Bug Tracker Articles:
http://www.securityweek.com/google-bug-tracker-exposed-details-unpatched-vulnerabilities