HomeHack: Hacking LG Smart Appliances
By Justin Cobbs on November 2, 2017

The rise of common appliance devices connected to the Internet, otherwise known as Internet of Things (IoT) devices, have made people’s lives convenient. They allow people the ability to control devices such as washing machines, dryers, refrigerators, air conditioners, etc from remote locations. Although IoT devices have made people’s lives convenient, it also makes it convenient for malicious attackers to take advantage of its capabilities with the remote attack surface. In fact, cybersecurity company Check Point disclosed a vulnerability on October 26 that they refer to as HomeHack. This vulnerability is with an IoT application owned by tech giant (LG) – commonly referred to as Life’s Good – called SmartThinQ.
Client-Side Vulnerability
According to researchers at Check Point, LG’s SmartThinQ application was vulnerable to a passive vulnerability on the client side of the application. This allowed the researchers to remotely take control of a user’s SmartThinQ account and all of the IoT devices the user owns and has linked to their account. One of the devices they decided to take control of was an automated home vacuum cleaner produced by LG called Hom-Bot. This is a multipurpose device which was designed to clean the homeowners rooms and act as a security device, since it has a built-in camera that displays a real-time video feed as it cleans.
Attack Process
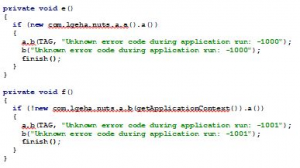
SmartThinQ source code is able to be returned when a user utilizes an Android Debug Bridge (ADB), according to Check Point. The malicious user could modify two sections of code to permit a rooted device from running the application by deleting the finish() function at the bottom of both sections.
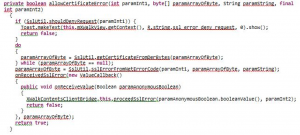
The malicious user could then modify a section of code that was responsible for implementing Secure Sockets Layer (SSL) pinning to prevent application traffic from being intercepted. Check Point did not specify how they patched it, but it seems likely that removing the block of code would work. Once the SSL pinning mechanism was bypassed, an attacker could intercept application traffic with their proxy to send their own login request.
The researchers utilized the source code and discovered that the login process is as follows:
- Authentication request – verifies user credentials.
- Signature request – creates a signature based on the username from authentication request.
- Token request – use the signature response as a header and username as parameter to get access token for the user account.
- Login request – sends the access token in order to login to the application.
Finally, the malicious could then craft their own request on the intercept to use their own LG account username and then switch it to the victim’s username on steps 2 and 3, since the application does not depend on step 1, to login to their account.
Secure Application Version
The HomeHack vulnerability was addressed by LG when they released application update version 1.9.23 at the end of September. Researchers at Check Point suggest that SmartThinQ application users update their application version to the latest version, which is 1.9.24 at the time of this writing. It is suggested that versions below 1.9.23 are vulnerable to the HomeHack attack surface, so it is a best practice to keep the application up-to-date. Check Point researchers also suggest that LG smart appliance owners update their physical devices with the most recent versions.
Sources
CheckPoint Analysis:
LG Smart ThinQ Info:
http://www.lg.com/us/discover/smartthinq/thinq
HomeHack Articles:
http://www.securityweek.com/security-flaw-could-have-let-hackers-turn-smart-ovens
https://thehackernews.com/2017/10/smart-iot-device-hacking.html
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025