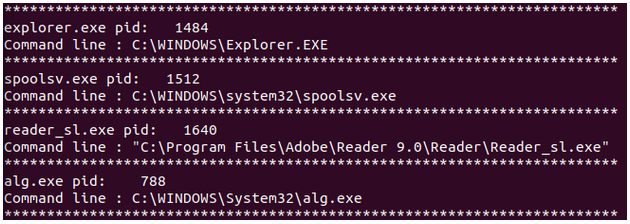
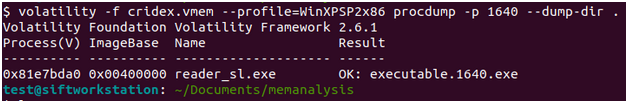
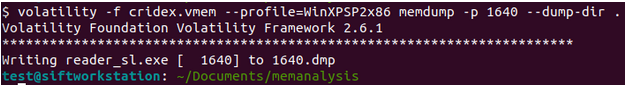
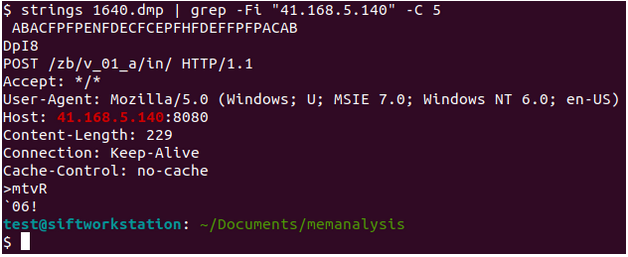
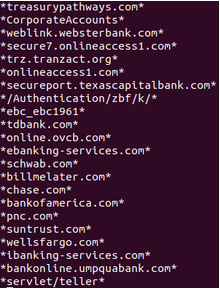
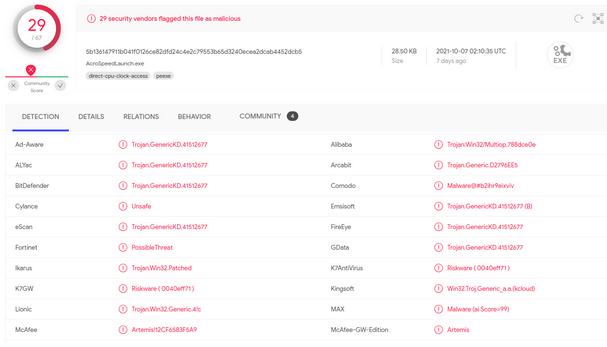
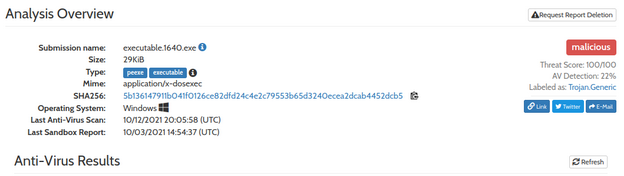
Memory CTF with Volatility Part 2
Related Posts
-
Importance of Digital Forensics Process Models: Some Examples
Importance of Digital Forensics Process Models: Some Examples
5/3/2024 -
Smart/IoT Devices as Evidence Sources
Smart/IoT Devices as Evidence Sources
4/16/2024 -
Applications and Challenges of Artificial Intelligence for Digital Forensics
Applications and Challenges of Artificial Intelligence for Digital Forensics
4/16/2024