The CyberWar Map and Other Cybersecurity Trackers
By MDL on September 18, 2018
Featured Cybersecurity Tracker: The CyberWar Map, National Security Archive

(The CyberWar Map Note: Please access this resource through the link on the Cyber Vault Project home page. Since each edition will have a new URL, bookmarking the CyberWar Map will not incorporate running updates.)
The CyberWar Map is associated with the Cyber Vault Project, an online repository of declassified or unclassified primary-source documents “obtained under the Freedom of Information Act and from other sources” documenting cyber activities of the U.S. and foreign governments. The Cyber Vault Project, funded by The Hewlett Foundation, is part of George Washington ’s National Security Archive.
The CyberWar Map, launched in June 2018, is an interactive map that uses data visualization to help users track global cybersecurity events, actors, government/organizational affiliations, targets, connections, affiliation, or attribution. The CyberWar Map also connects to supporting documents found in the Cyber Vault Library and publications from cybersecurity researchers and news organizations. The map is especially useful for identifying APT aliases, learning about unfamiliar cybersecurity events, and tracking what the creators call “state-to-state cyberconflict.”
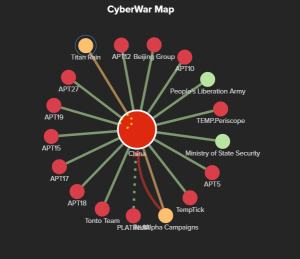
Clicking on a flag, dot, or line causes the side panel to load relevant information including links to related documents. The sidebar default shows a list of links for “Nations” which includes groups that operate beyond a country’s borders, for example, Al Qaeda, and ISIS. The “Focus” option allows users to see only information related to a specific node.
 The CyberWar Map is based on a mindmap and is not meant to resemble a geographical map. This abstraction of dots and lines can help users identify surprising connections that might be overlooked when reading an article or consulting a spreadsheet or database.
The CyberWar Map is based on a mindmap and is not meant to resemble a geographical map. This abstraction of dots and lines can help users identify surprising connections that might be overlooked when reading an article or consulting a spreadsheet or database.
Although the map connects to some declassified US government Cyber Vault documents, the majority of the documents offered for specific cyber events come from news organizations or security researchers. Often there is only a single source listed for a cyber event. The CyberWar map also deals with more recent cyber events. The earliest event article found was dated 2010. This map also seems to lag slightly behind the documents made available in the Cyber Vault which seems to be extremely timely and current to the day of document release.
More Cybersecurity Trackers
Cyber Operations Tracker
Digital and Cyberspace Policy Program
Council on Foreign Relations
![]()
https://www.cfr.org/interactive/cyber-operations
“The cyber operations tracker categorizes all instances of publicly known state-sponsored cyber activity since 2005. The tracker only contains data in which the perpetrator, also known as the threat actor, is suspected to be affiliated with a nation-state.”
APT Groups and Operations spreadsheet
Florian Roth
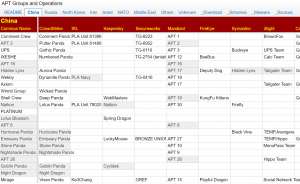
https://docs.google.com/spreadsheets/d/1H9_xaxQHpWaa4O_Son4Gx0YOIzlcBWMsdvePFX68EKU/pubhtml
“Cyber security companies and Antivirus vendors use different names for the same threat actors and often refer to the reports and group names of each other. However, it is a difficult task to keep track of the different names and naming schemes. I wanted to create a reference that answers questions like “I read a report about the ‘Tsar Team’, is there another name for that group?” or “Attackers used ‘China Chopper’ webshell, which of the APT groups did use that shell too?” or “Did he just say ‘NetTraveler’? So, does he talk about Chinese or Russian attackers?””
Significant Cyber Incidents
Center for Strategic and International Studies (CSIS)

“This timeline records significant cyber incidents since 2006. We focus on cyber attacks on government agencies, defense and high tech companies, or economic crimes with losses of more than a million dollars.”
Targeted Cyberattacks Logbook
Kaspersky Securelist

https://apt.securelist.com/#!/threats/
“Kaspersky Lab’s Targeted Cyberattack Logbook chronicles all of these ground-breaking malicious cybercampaigns that have been investigated by GReAT.”
-
Hackers Steal $500,000 from Australian Super Funds
Hackers Steal $500,000 from Australian Super Funds
4/11/2025 -
U.S. Department of Justice Seizes 8.2 Million in Cryptocurrency
U.S. Department of Justice Seizes 8.2 Million in Cryptocurrency
4/4/2025 -
Interpol Arrests Over 300 for Cyber Crimes in Africa
Interpol Arrests Over 300 for Cyber Crimes in Africa
4/4/2025