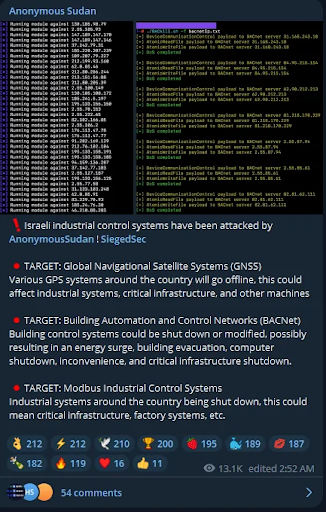
Anonymous Sudan Targets Israel’s Critical Infrastructure
Related Posts
-
Hackers Steal $500,000 from Australian Super Funds
Hackers Steal $500,000 from Australian Super Funds
4/11/2025 -
U.S. Department of Justice Seizes 8.2 Million in Cryptocurrency
U.S. Department of Justice Seizes 8.2 Million in Cryptocurrency
4/4/2025 -
Interpol Arrests Over 300 for Cyber Crimes in Africa
Interpol Arrests Over 300 for Cyber Crimes in Africa
4/4/2025