CrossRAT, A new cross platform malware
By Robert Kuakini on January 26, 2018

A detailed security research report on the advanced persistent threat, Dark Caracal was published by Lookout and the Electronic Frontier Foundation(EFF) on January 18, 2018. The report contained background information about the group as well as many of the components and tools they had at their disposal. One noteworthy tool was a new remote access trojan called CrossRAT found during an investigation into the axroot[.]com domain. It is one of many cyber-espionage tools that had been developed by or for them.
Key Functions
- Cross-platform deployment, targeting Windows, Linux, and OSX operating systems
- Manipulate file systems
- Take screenshots
- Run arbitrary DLLs for secondary infection on Windows
- Gain persistence on the infected system
- Communicate to it Command and Control server via TCP socket
The most notable of these functions is the ability for it to execute on a wide range of platforms, giving Dark Caracal, or any other threat more targets and flexibility in conducting espionage activities.
Technical Analysis
The following technical information is taken from the Lookout/EFF report.
In regards to Windows environments,
when CrossRAT is executed in a Windows environment it attempts to copy itself to %AppData%Local Tempmediamgrs.jar then creates an auto-start registry key in HKEY_USERSSoftwareMicrosoftWindowsCurrentVersionRun with the name “mediamgrs”.
In regards to OSX, and Linux environments,
it attempts to write a copy of itself to /usr/var/mediamgrs.jar. If CrossRAT does not have sufficient permissions to write to this directory, it will fail back to the following path under the user’s home directory: $HOME/Library/mediamgrs.jar. For CrossRAT installations on OSX, a Launch Agent is created under $HOME/Library/ LaunchAgents/mediamgrs.plist to ensure that it will be launched again when the computer restarts. When on Linux, this persistence is achieved by writing an autorun file to $HOME/.config/autostart/mediamgrs.desktop.
In order to communicate with its C2 infrastructure, CrossRAT uses TCP sockets to send structured messages. Below is an example of content sent from a compromised machine to the server.
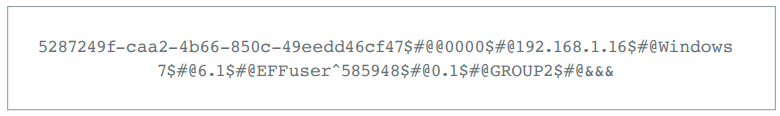
According to Lookout/EFF the above snippet uses a specific infrastructure. It uses &&& to terminate the response string and uses @### to start command strings.
Analysis of CrossRAT
A March 2017 sample of CrossRAT was analyzed and provided key insight into the structure and features of the malware. The analysis showed that it has a version number of 0.1, indicating that the malware is still in early development. Some of the information found were prefixed responses, and hard corded C2/port information.
Additionally, having been written in the Java programming language, allowed decompiling and analyzing to be relatively straightforward. Digita Security’s, Patrick Wardle offers a detailed breakdown of CrossRAT from decompiling methods to explanation of code segments. The blog post focuses on identifying and understanding the persistence mechanism (and install location), C&C communications, and features/capabilities.
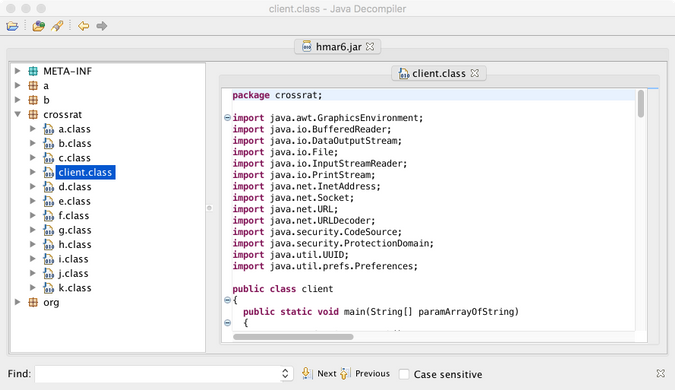
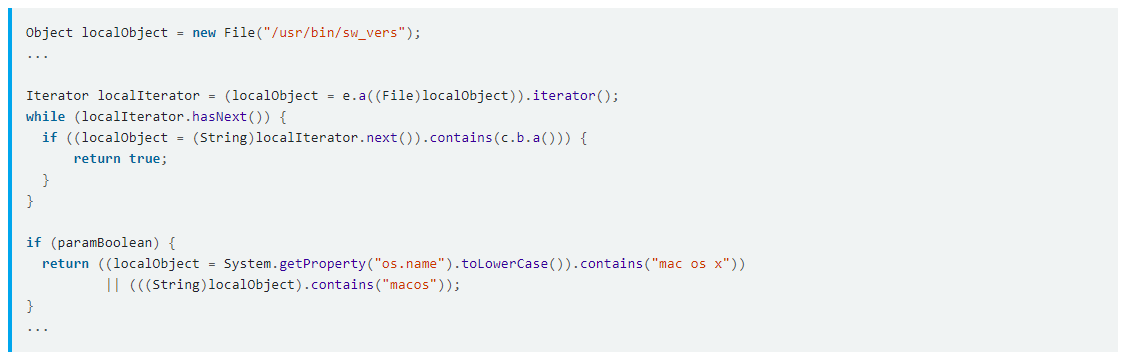
The full analysis from Digita Securitys and Patrick Wardle can be found here. It is highly recommended to follow the breakdown process as it shows in depth detail of how CrossRAT operates.
Distribution
The Look/EFF reported the primary distribution method of of Dark Caracal,
They rely primarily on social media, phishing, and in some cases physical access to compromise target systems, devices, and accounts.
This deployment method while not entirely sophisticated is an effective way to distribute the malware.
Detection
Here are a few ways to tell if you’re infected with CrossRat:
For Windows:
- Check the ‘HKCUSoftwareMicrosoftWindowsCurrentVersionRun’ registry key.
- If infected it will contain a command that includes, java, -jar and mediamgrs.jar.
For macOS:
- Check for jar file, mediamgrs.jar, in ~/Library.
- Also look for launch agent in /Library/LaunchAgents or ~/Library/LaunchAgents named mediamgrs.plist.
For Linux:
- Check for jar file, mediamgrs.jar, in /usr/var.
- Also look for an ‘autostart’ file in the ~/.config/autostart likely named mediamgrs.desktop.
Mitigation
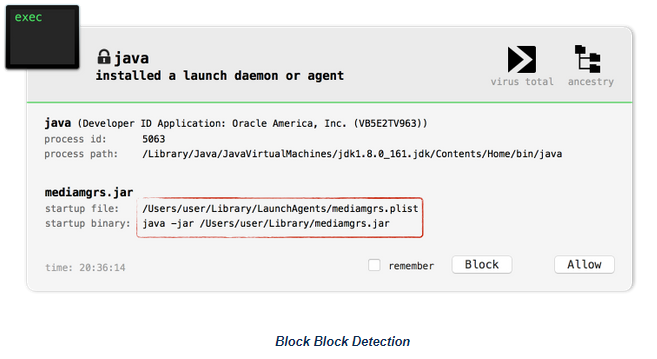
Currently, as of writing this summary, anti-virus is not a viable method of detection/protection against a CrossRAT infection as the detection rate is quite low. This should change as time progresses, and more detectable signatures are to be crafted. Despite this Digita Security suggested that behavior detections tools focused on persistence should help in detection. An example of one is BlockBlock for OSX.
Conclusions
So while CrossRAT does pose a significant threat by being able to execute on a wide range of platforms, the overall analysis of CrossRAT is relatively straightforward from decompiling the actual malware to understanding its features. With information about it being released to the public awareness and detection can be improved. However, it is important to note that CrossRAT is in version 0.1 and could still be in development, or used by other threats. We could be seeing improved versions or variants in the foreseeable future.
Sources
https://thehackernews.com/2018/01/crossrat-malware.html
https://digitasecurity.com/blog/2018/01/23/crossrat/
https://info.lookout.com/rs/051-ESQ-475/images/Lookout_Dark-Caracal_srr_20180118_us_v.1.0.pdf
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025