BlueBorne Able to Affect Amazon Echo and Google Home
By Justin Cobbs on November 22, 2017
 Approximately two and a half months ago Armis, an Internet of Things (IoT) cybersecurity research company, disclosed BlueBorne – Bluetooth implementation vulnerabilities that affected Windows, Android, Linux, and iOS devices. These Bluetooth vulnerabilities ultimately allow an attacker to remotely execute code, obtain sensitive information, or conduct man-in-the-middle (MitM) attacks against these devices. Recently, Armis discovered that around a total of 20 million Amazon Echo and Google Home, smart speaker voice-activated personal assistant IoT devices, are also susceptible to MitM BlueBorne attacks. According to Armis, Amazon Echo devices are vulnerable to CVE-2017-1000251: Linux Kernel Bluetooth Stack Overflow and CVE-2017-1000250: Sessions Description Protocol (SDP) Server Bluetoothd Process Sensitive Information Disclosure. The Google Home devices are vulnerable to CVE-2017-0785: Android Bluetooth Stack Sensitive Information Disclosure.
Approximately two and a half months ago Armis, an Internet of Things (IoT) cybersecurity research company, disclosed BlueBorne – Bluetooth implementation vulnerabilities that affected Windows, Android, Linux, and iOS devices. These Bluetooth vulnerabilities ultimately allow an attacker to remotely execute code, obtain sensitive information, or conduct man-in-the-middle (MitM) attacks against these devices. Recently, Armis discovered that around a total of 20 million Amazon Echo and Google Home, smart speaker voice-activated personal assistant IoT devices, are also susceptible to MitM BlueBorne attacks. According to Armis, Amazon Echo devices are vulnerable to CVE-2017-1000251: Linux Kernel Bluetooth Stack Overflow and CVE-2017-1000250: Sessions Description Protocol (SDP) Server Bluetoothd Process Sensitive Information Disclosure. The Google Home devices are vulnerable to CVE-2017-0785: Android Bluetooth Stack Sensitive Information Disclosure.
Attack Process
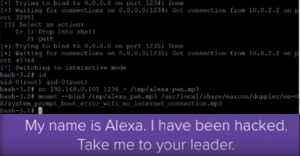
The YouTube Proof of Concept (PoC) video that Armis provided demonstrates a generic attack process for remotely exploiting an Amazon Echo device. First a malicious actor would launch a custom script that takes advantage of the BlueBorne vulnerability using the Bluetooth Media Access Control (MAC) address of the Echo device. The malicious actor would then be connected and running the device on the highest permission level of root. From this point on, the malicious actor could upload a file onto the Echo device by having it transferred on a specified port using the Netcat command. Once the file has been uploaded and mounted, the Echo device would take the input and apply it without any warning. In the video above, the PoC showed that the personal assistant on the Echo, Alexa, was reprogrammed to say that she has been hacked when someone says “Alexa”.
Mitigations
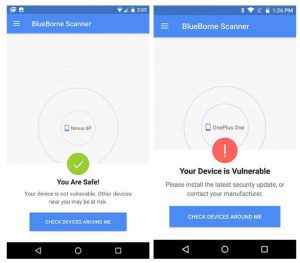
The Bluetooth features native on Amazon Echo and Google Echo are unable to be disabled. Both smart speaker personal assistant devices are also incompatible with antivirus software. These restrictions make it difficult to prevent or mitigate system device vulnerabilities, so the only known mitigation is to hope that Amazon and Google provide software patches that address vulnerabilities. The good news is that these two IoT devices automatically receive and install software updates. For the Amazon Echo, users can verify that their device has been patched by having a version newer than v591448720. Armis did not specify which version of Google Home is secure from the BlueBorne attack, so it is best to have the most current updates applied. Armis also has a BlueBorne vulnerability scanner available on the Google Play Store that scans nearby devices for devices vulnerable to the attack, so that users can apply software updates to mitigate the vulnerabilities.
Sources
Common Vulnerabilities and Exposures (CVE):
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-1000251
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-1000250
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0785
BlueBorne:
https://www.armis.com/blueborne/
http://www.securityweek.com/billions-devices-potentially-exposed-new-bluetooth-attack
Echo and Home Articles and Advisory:
http://www.securityweek.com/amazon-echo-google-home-vulnerable-blueborne-attacks
https://thehackernews.com/2017/11/amazon-alexa-hacking-bluetooth.html
https://www.armis.com/blueborne-cyber-threat-impacts-amazon-echo-google-home/
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025