Ledger Cryptocurrency Wallet Flaw
By Robert Kuakini on March 23, 2018
What happened?
Security researcher, Saleem Rashid discovered a critical flaw in cryptocurrency wallet hardware created by the company, Ledger. A hardware wallets purpose is to protect a users cryptocurrency private wallet address from being stolen by malicious software located on a computer. It prevents the computer from being to read the wallet address but still receives the authentication that it is legitimate. Rashid’s work was reviewed by cryptographer Matthew Green, and Open Crypto Audit Projects Kenneth White who were impressed by Rashid’s proof of concept exploit. It was created to take advantage of this flaw to show the extent of this compromise showing an attacker could use this flaw to alter the device before a user receives it, or to steal the wallet keys locally or remotely.
Several potential attacks against these devices were discussed in a document released by Rashid.
- Supply Chain Attack
- Evil Maid Attack
- Malware/Social Engineering
The focus of the published paper was the supply chain attack with attacks being demonstrated on a real Ledger Nano S. While the focus is on software, compromising the devices hardware is extremely viable.
A video was provided by Rashid performing the attack and altering one such device physically.
As you can tell from the video above, it is trivial to perform a supply chain attack that modifies the generated recovery seed. Since all private keys are derived from the recovery seed, the attacker could steal any funds loaded onto the device.
A less reliable proof of concept code was released by Rashid to Github for educational purposes.
Technical Details
Key Aspects
- Microprocessor chip is not secure.
- Proof-of-concept code bypasses security measures.
- Buttons and screen can be reprogrammed.
- Authentication between the secure element and micro-controller is not strong enough.
The vulnerability comes from a flaw in how Ledger designed their dual-chip architecture. The secure element micro-controller initially used does not support the needs of their hardware. In order to remedy this they designed one of their own to compensate. The micro-controller has been shown to be non-secure and susceptible to attacks which Rashid focuses on.
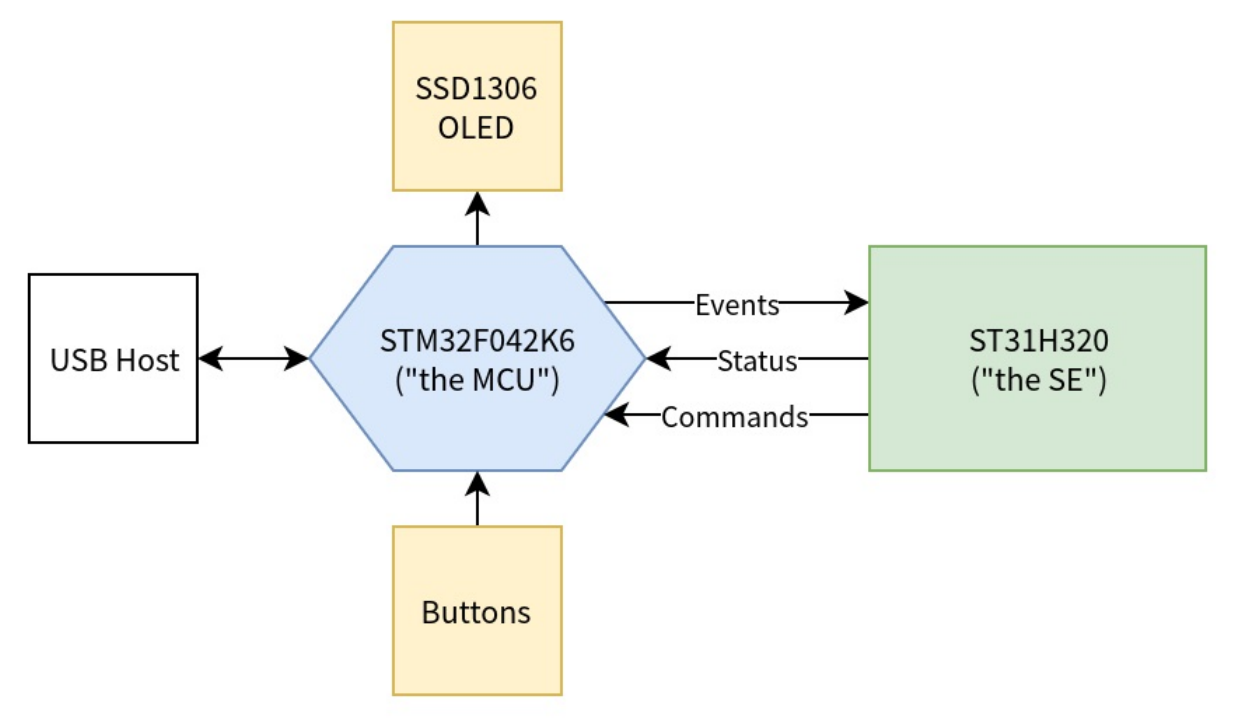
The Nano S has two micro-controllers.
- ST31H320 (SE) – Secure Element but does not support displays or USB. Stores private keys.
- STM32F042K6 (MCU) – non-secure micro-controller which acts as a proxy for the SE and processes the display, buttons and USB interface.
Due to the MCU being vulnerable it puts other devices, peripherals, and the SE at risk. Below a diagram of how the communication takes place.
Ledgers Security
Ledger does have security measures in place to verify the integrity of the MCU’s firmware by using a low-throughput universal asynchronous receiver-transmitter(UART). The SE asks the MCU for the entire contents of its flash memory to verify it contains official Ledger firmware. The security theory is that with only a limited amount of flash memory available that it would be difficult to run the official Ledger firmware and malicious code at the same time. A diagram of this method can be seen below.
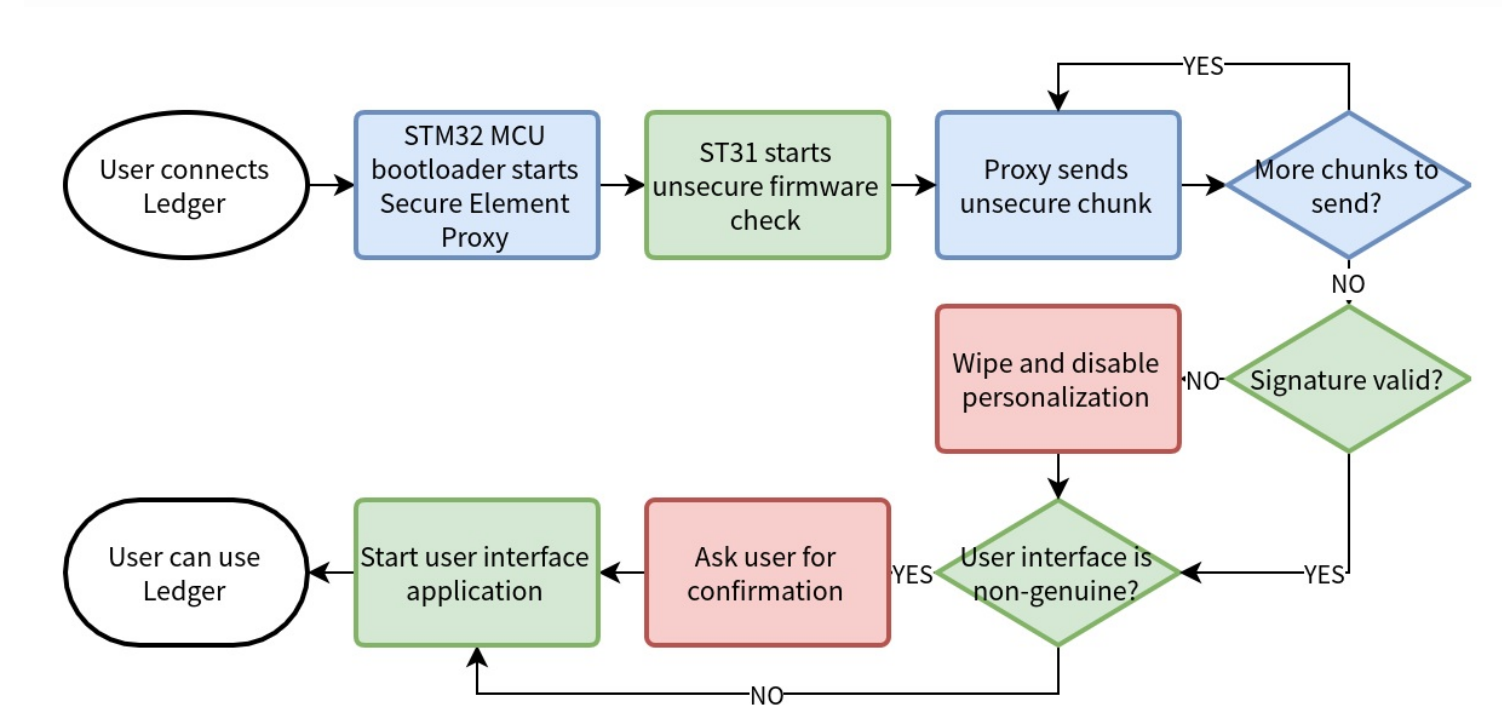
Rashid having studied Ledgers method of defense designed an attack exploit. However it should be noted that malicious code from a malicious USB would be a more direct route he set out to create his own software code. He understood that C programs, in order to use some functions will often provide itself with extra programs and in this case it was a bootloader and firmware.
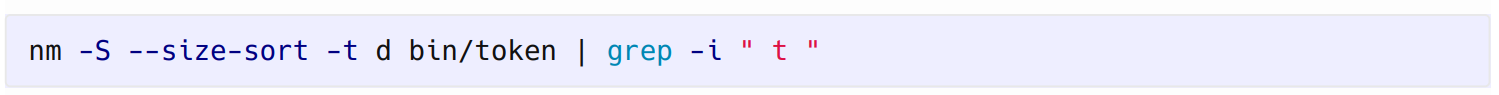
To exploit this Rashid created his own bootloader and firmware from source code using the command below to find the appropriate symbols.
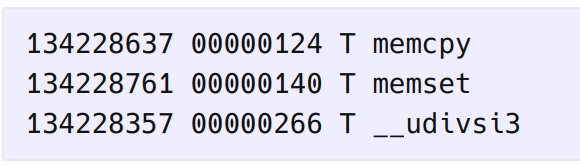
He combined malicious branches that included the payload and targets with the malicious code. By using the appropriate code at the correct time the malicious code is able to be loaded without any issues. This can be seen in the diagram below on how he uses the “__udivsi3” as the attack vector.
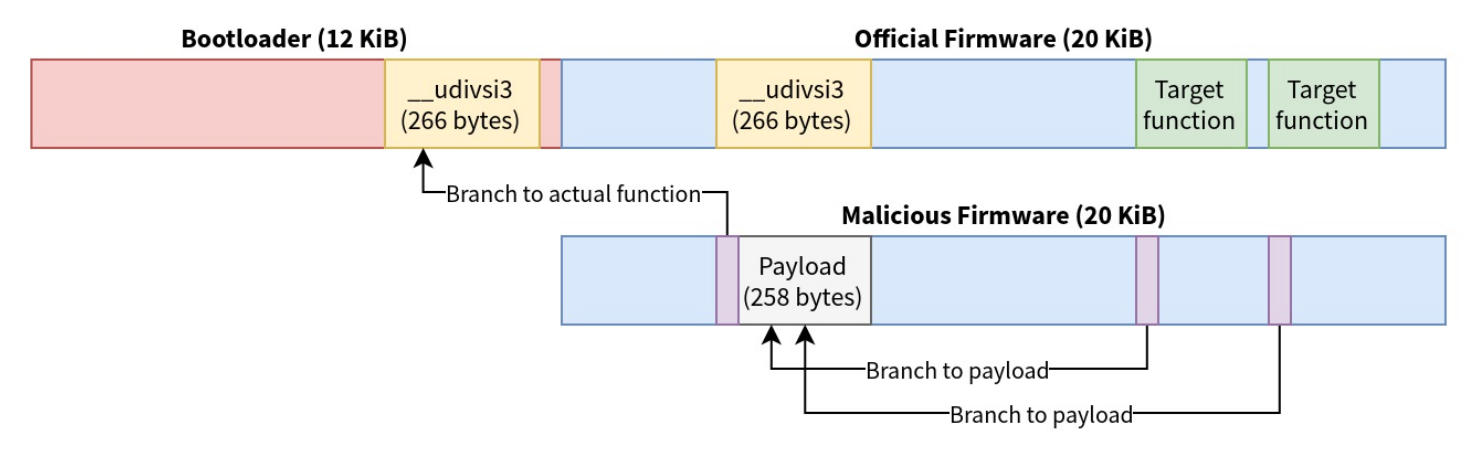
After using the vulnerability to get into the device Rashid creates an exploit to:
- Code to modify the flash contents being sent to the SE, to trick the verification procedure
- An attack such as a keylogger or key generation backdoor
The exploit code he wrote is below.
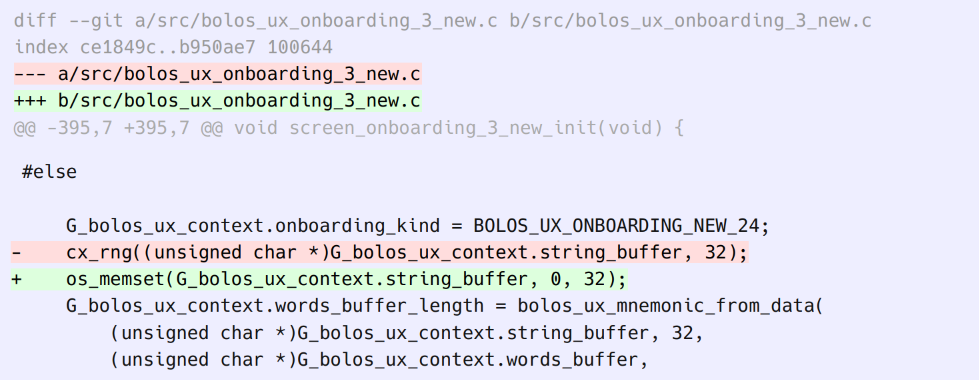
The code sets all entropy of the syscall random number generator to zero. It sets the recovery seed to the word “abandon”. Private keys are derived from the recovery seed and if you control the seed then you essentially control all the wallet addresses generated by the device.
A diagram of the SE/MCU communication with the malicious code can be found below.
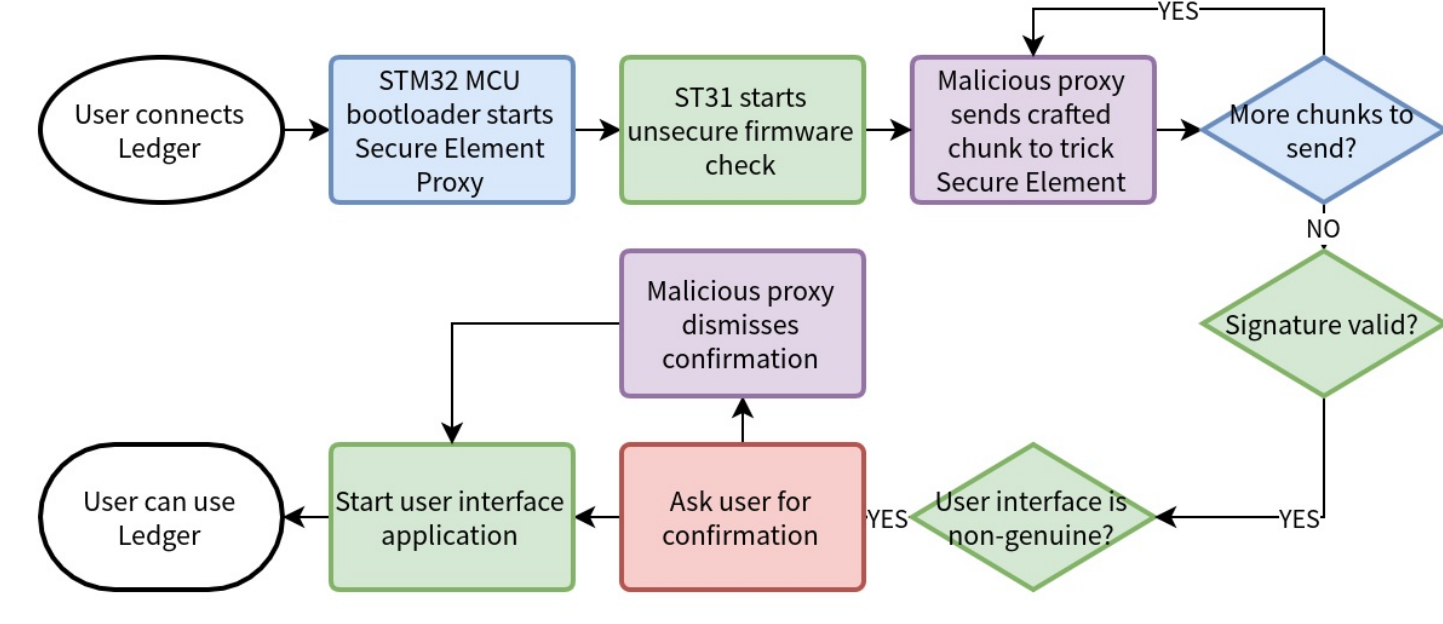
Mitigation
- Secure design and testing – The root of the vulnerabilities can be derived from the architecture design. If there were proper testing of the MCU and the other components this type of issue could have been avoided.
- Firmware update – Ledger is releasing a firmware update to fix the vulnerabilities.
Significance
The vulnerability and exploits only directly affects current users of Ledgers crypto wallets. However, this type of vulnerability does bring light to the ongoing design and architecture issues currently taking place. While nothing is completely secure there should be safeguards in place to protect the sole purpose of these wallets. It is important for developers and companies to begin securing their products at the hardware level and properly testing them before releasing to the public.
Sources:
https://krebsonsecurity.com/2018/03/15-year-old-finds-flaw-in-ledger-crypto-wallet/
https://krebsonsecurity.com/wp-content/uploads/2018/03/ledgerattack.pdf
http://www.st.com/en/secure-mcus/st31h320.html
https://github.com/LedgerHQ/nanos-nonsecure-firmware
-
CISA Issues Emergency Directive In Light of New Cisco Vulnerabilities
CISA Issues Emergency Directive In Light of New Cisco Vulnerabilities
10/10/2025 -
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025