High Sierra OS Plaintext Bug
By Robert Kuakini on April 6, 2018
What happened?
Forensic Analyst Sarah Edwards discovered a flaw in the Apple File System (APFS) within Apple’s High Sierra operating system. It was discovered that newly encrypted APFS volumes were displaying plaintext passwords used on these volume through the use of a simple command.
The above image is of an APFS formatted FileVault Encrypted USB drive with the volume name “SEKRET” and the password “frogger13”.
Apple File System
Apple File System is a new, modern file system for iOS, macOS, tvOS, and watchOS. It is optimized for Flash/SSD storage and features strong encryption, copy-on-write metadata, space sharing, cloning for files and directories, snapshots, fast directory sizing, atomic safe-save primitives, and improved file system fundamentals.
APFS replaces HFS+ as the default file system for iOS 10.3 and later, and macOS High Sierra and later.
Technical Information
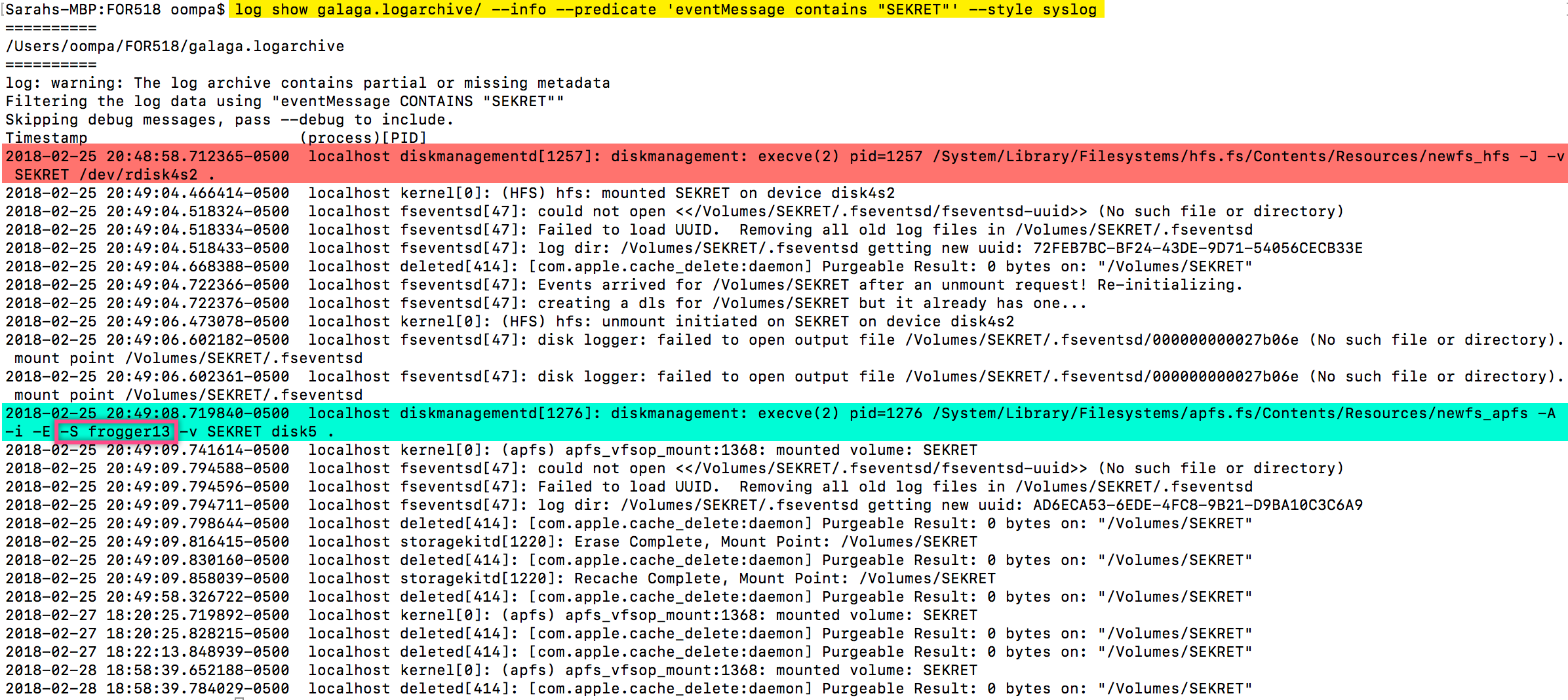
Sarah investigated this issue further by examining the command, “ newfs_apfs”. The command “creates a new AFPS container on the device and/or address a new APFS volume to a container”. She discovered a lightly documented command “-S” flag. The man page for the newfs_apfs does not display documentation of the “-S” flag but it does appear when no arguments are run with the command.
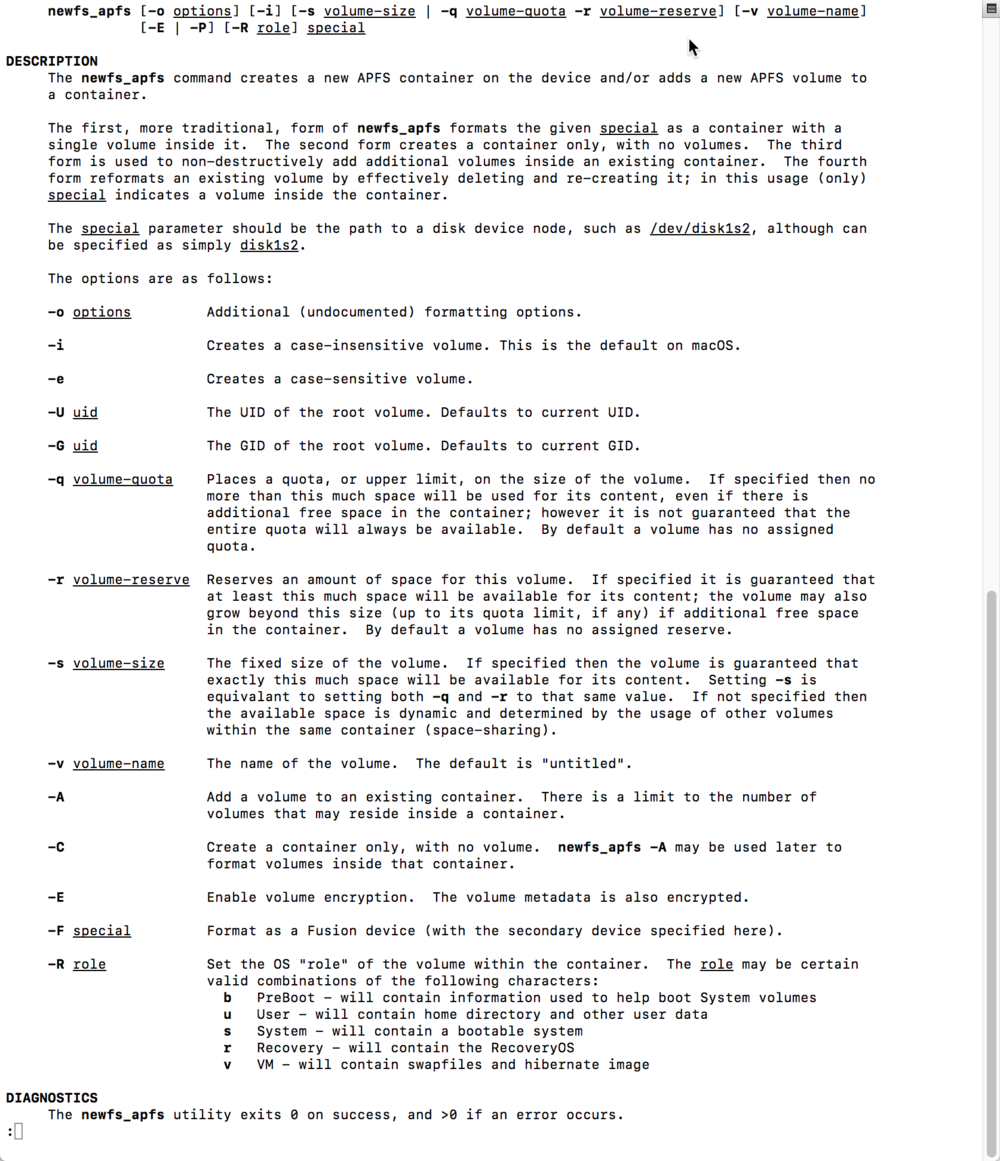

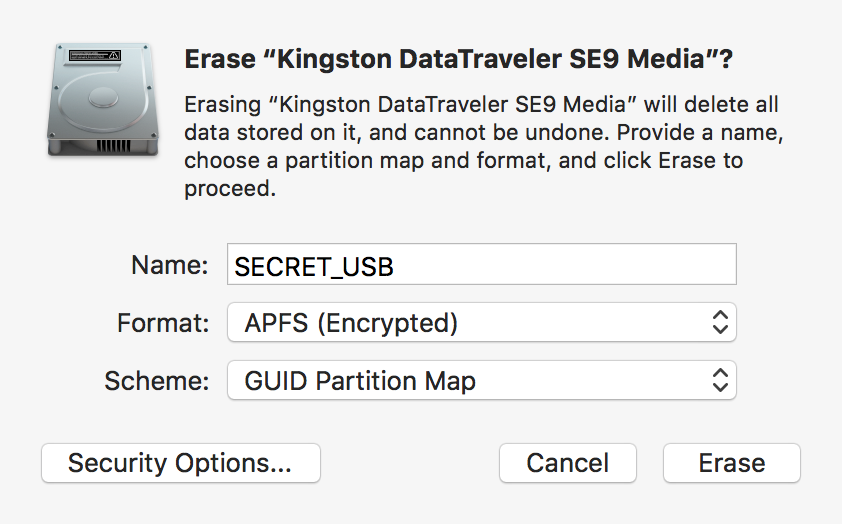
To test this flaw, she started with a clean flash drive, formatted it to a “Mac OS Extended (Journaled)” the converted it to a APFS encrypted format named “SECRET_USB”
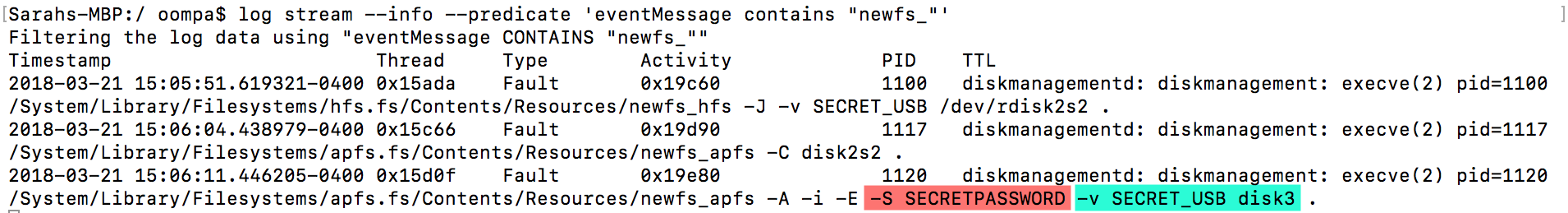
She then used the command “log stream –info –predicate ‘eventMessage contains “newfs_”‘ which monitors the APFS encryption and eventually displaying the volumes name and the password.
Significance
The passwords are being stored in an unsecured way and can be harvested by those with malicious intent. This can be conducted through physical access to the machine or through malware set to harvest log files.
Mitigation
Apple is aware of this issue and released a security bulletin. According to the bulletin, Apple released a security update on March 29th, 2018 addressing the APFS flaw. The most effective mitigation is to update your macOS to the latest patch. However, it should be noted that Forensic Analyst Sarah Edwards as well as others are currently digging deeper into this issue and not all instances of this bug have been patched. As more testing is being conducted this bug is not completely patched as of this current date. As previously stated keeping your system up to date is still the best way to prevent this bug.
Conclusion
This vulnerability is one of many found on the macOS High Sierra such as the bug that lets any user gain root and another one that shows the displays a password in the hint section. It is not clear if these flaws are due to the way the APFS is built or if security testing was properly conducted but these password related flaws are starting to become an increasing trend. Despite this, Apple has remained vigilant and has made significance attempts to mitigate these issues as quickly as possible.
Sources:
The Hacker News, https://thehackernews.com/2018/03/macos-apfs-password.html
Security Week, https://www.securityweek.com/macos-high-sierra-logs-external-volume-passwords-plaintext
Apple Support, https://support.apple.com/en-us/HT208692
NVD, https://nvd.nist.gov/vuln/detail/CVE-2018-4105
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025