Weekly Executive Summary for Week November 24, 2017
By Joseph Lorenz on November 27, 2017
Blocking Phase:
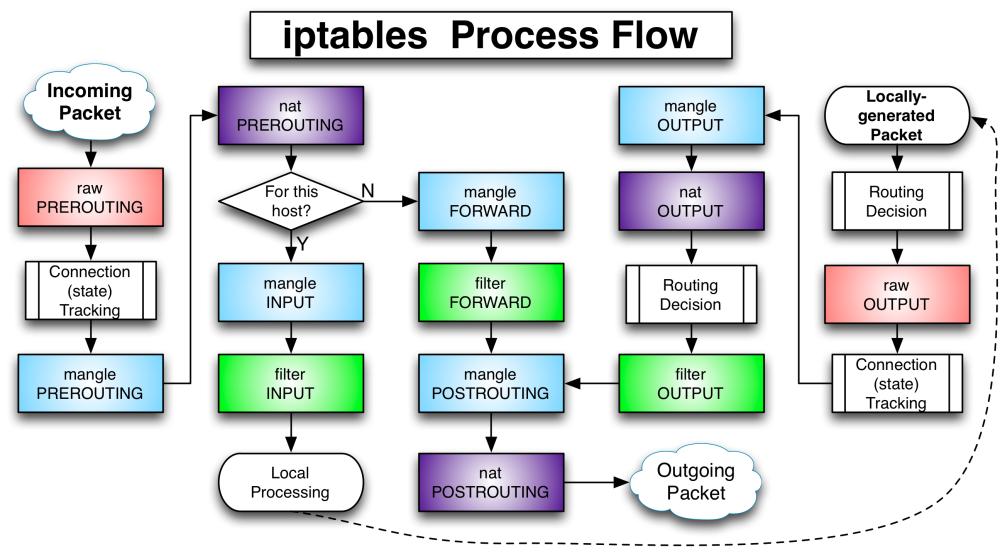
The final phase in the ORB application uses a python library called python-iptables. Iptables is a tool used to manage netfilter, which is used for packet filtering and manipulation in Linux. Rules are created and packets are matched based on their contents and actions are taken based on these rules.
Source: n0where
Every packet that enters the networking system will trigger hooks in the Linux kernel’s networking stack. Hooks will trigger depending on whether the packet is incoming or outgoing, the packets destination, and whether the packet was dropped or rejected in a previous point of the stack. IPTables firewall uses tables to organize its rules and will classify rules according to types of decisions the rules will make. This application will primarily use the filter table which is used to make decisions on whether to let a packet continue to its intended destination or deny its request.
[cc lang=”python” width=”100%”]
import iptc
ip_block = ‘192.168.18.177’
[/cc]
An IP address is set for an iptable rule and the python-iptables library is imported
[cc lang=”python” width=”100%”]
chain = iptc.Chain(iptc.Table(iptc.Table.FILTER), “INPUT”)
rule = iptc.Rule()
[/cc]
The chain object is created on INPUT (all traffic coming into the network) and is applied to the FILTER table
[cc lang=”python” width=”100%”]
rule.in_interface = “eth+”
rule.src = ip_block + “/255.255.255.0″
[/cc]
A interface is set, in this case it is all eth or ethernet interfaces and the IP address and subnet mask are applied to the rules src or source
[cc lang=”python” width=”100%”]
target = iptc.Target(rule, “DROP”)
[/cc]
The target rule is set to DROP all packets if detected by the earlier rule.src IP address
[cc lang=”python” width=”100%”]
rule.target = target
chain.insert_rule(rule)
[/cc]
The rule for the target is created and is inserted into a chain in the ruleset
Once a target IP has been determined by the scanning phase, the IoT device will be monitored for all incoming traffic using the monitoring phase. If network traffic is detected targeting an IP address in the trusted list a user is given the ability to accept or block that traffic. If a user chooses to block traffic from an untrusted source a rule is created on in the FILTER table to DROP packets to the IoT device.
Sources:
https://n0where.net/how-does-it-work-iptables/ (n0where)
https://github.com/ldx/python-iptables (python-iptables)
https://github.com/buckyroberts/Python-Packet-Sniffer (Packet Sniffer)