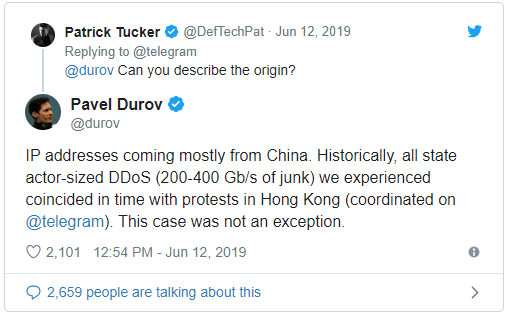
China “Xi’s” Red: Cyber Warfare Used on Hong Kong Protestors
Related Posts
-
Cyber Attacks and Disinformation Threaten Taiwan
Cyber Attacks and Disinformation Threaten Taiwan
10/24/2025 -
North Korean Crypto Theft Peaks in 2025
North Korean Crypto Theft Peaks in 2025
10/17/2025 -
UK Schools Experiencing Increased Breaches and Attacks
UK Schools Experiencing Increased Breaches and Attacks
10/10/2025