Global Weekly Executive Summary, 02 November 2018
By MDL on November 7, 2018
China Telecom and BGP Hijacking
In an article in Military Cyber Affairs, researchers claim to have uncovered evidence that China Telecom has been deliberately using Border Gateway Protocol (BGP) hijacking to selectively divert internet traffic originating in the US and Canada through China.
Source: Military Cyber Affairs, China’s Maxim – Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking
- In their article in Military Cyber Affairs, The Journal of the Military Cyber Professionals Association, Dr. Chris Demcheck, Director of the Center of Cyber Conflict Studies at the US Naval War College, and Dr. Yuval Shavitt, Professor of Electrical Engineering at Tel Aviv , suggest that China has found a way to gather valuable information from US organizations while still technically adhering to the 2015 US-China Cyber Agreement.
- In the voluntary 2015 US-China Cyber Agreement, China’s President Xi Jinping agreed that Chinese military forces would cease hacking US commercial organizations for financial gain.
- Demcheck & Shavitt’s article describes how the researchers used a special route tracing system for monitoring BGP announcements to identify “unusual and systemic hijacking patterns associated with China Telecom.” They say their findings show the China Telecom “has already relatively seamlessly hijacked domestic US and cross-US traffic and redirected it to China over days, weeks, and months.”
- The route tracing system, based at Tel Aviv , was built for DIMES, a project to study and map the structure and topology of the internet.
BGP
- Border Gateway Protocol (BGP) is an internet routing protocol that requires using the shortest route to move data traffic between the source and the destination IP addresses. “Forwarding tables,” built by servers hosting BGP, are used to determine the shortest route and the path that packets should travel between the smaller autonomous networks (AS) by passing through internet points-of-presences (PoPs).
- A ZDnet article explains it simply, “PoPs are data centers that do nothing more than re-route traffic between all the smaller networks that make up the larger internet.” “Traffic travels between these AS networks with the help of the Border Gateway Protocol (BGP),” a protocol created in the early 1980s and lacking in security controls.
- BGP misconfiguration errors can happen easily, and traffic can sometimes be rerouted in ways that can have, what Demcheck & Shavitt describe as, “almost global effects.”
- As an example, the researchers describe the 2008 Pakistan Telecom error that “accidentally hijacked all Youtube traffic for several hours as administrators make mistakes in using routing to censor a clip considered non-Islamic.”
BGP Hijacking
- BGP hijacking occurs when false BGP announcements are made intentionally with malicious intent.
- BGP hijack attacks are a type of man-in-the-middle attack and are difficult to distinguish from accidental router misconfigurations, but Demcheck & Shavitt say that the route tracing system they used allowed them to identify what a Sophos article described as “a series of unusual routing events that they believe were too consistent in their duration and scale to be dismissed as accidents.”
- BGP hijack attacks are also difficult to detect and protect against because, “it is not a hack of the endpoint but of the critical exchanges carrying information between end points.” Users do not need to click on a bad link, and network administrators cannot see any changes in data transfer patterns. Sensitive and valuable data could rerouted, copied and collected, and forwarded to the correct destination with only a brief delay.
- According to Demcheck & Shavitt, “most BGP hijacks are the work of government agencies or large transnational criminal organizations with access to, leverage over, or control of strategically placed ISPs.”
China Telecom
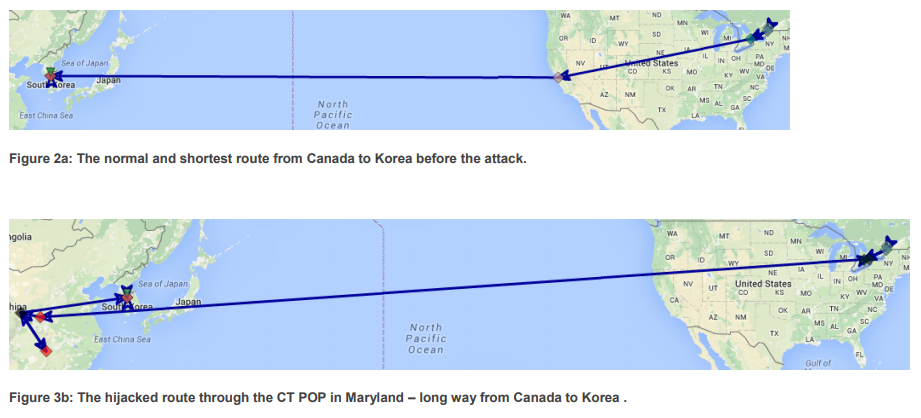
- China Telecom is a large telecommunications company based in China but with ten Chinese-controlled internet “points of presence” (PoPs) across North America, eight in the US, two in Canada. According to the China Telecom Americas website, their PoPs were first established in the US in 2000.
- According to Demcheck & Shavitt, in 2010 China Telecom hijacked 15% of the Internet traffic for 18 minutes in what is believed to be both a large-scale experiment and a demonstration of Chinese capabilities in controlling the flows of the internet.
- Feb- Aug 2016 “routes from Canada to Korean government sites were hijacked by China Telecom and routed through China.”
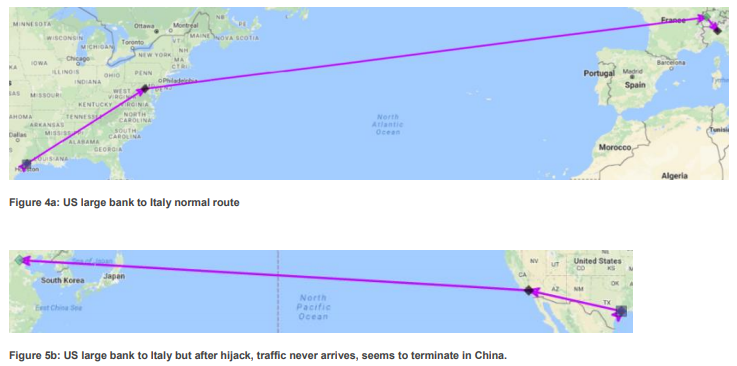
- October 2016, traffic from several locations in the USA to a large bank headquartered in Milan, Italy was hijacked by China Telecom to China.
- April/May 2017, Traffic from Sweden and Norway to the Japanese network of a large American news organization was hijacked to China
- April, May, and July 2017, Traffic to the mail server (and other IP addresses) of a large financial company in Thailand was
hijacked several times
Source: Military Cyber Affairs, China’s Maxim – Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking
Significance and Analysis
This article shows that internet communications can be vulnerable in ways that cannot be easily detected and cannot be prevented. The researchers, Demcheck & Shavitt, highlight the possible impact that China’s use of BGP hijacking can have on data confidentiality and availability, but the problem could be much larger than the instance described. Data integrity could also be affected, and China may not the only country attempting to use BGP hijacking to snoop on data sent across the internet.
Demcheck & Shavitt discussed how BGP hijacking could cause network traffic to be rerouted so that it could be intercepted, copied, and sent on without either sender or receiver noticing, but they also described one instance of traffic being rerouted and never reaching the intended recipient. Data from US companies or from anyone could conceivably be intercepted, copied, and held so that the recipient never received it, all without the original sender or the intended recipient knowing anything is amiss.
A Sophos blog post on this subject offers the following advice, “One defence against BGP hijacking is TLS encryption. It doesn’t stop the rerouting but if someone diverts web, email or DNS traffic encrypted with TLS through their POP it should be unreadable.”
Sources
The White House, FACT SHEET: President Xi Jinping’s State Visit to the United States
Military Cyber Affairs, China’s Maxim – Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking
Sophos, Naked Security Blog, China hijacking internet traffic using BGP, claim researchers
Yuval Shavitt and Eran Shir, DIMES: Let the Internet Measure Itself (PDF)
ZDnet, China has been ‘hijacking the vital internet backbone of western countries’
China Telecom Americas, History
-
Hackers Steal $500,000 from Australian Super Funds
Hackers Steal $500,000 from Australian Super Funds
4/11/2025 -
U.S. Department of Justice Seizes 8.2 Million in Cryptocurrency
U.S. Department of Justice Seizes 8.2 Million in Cryptocurrency
4/4/2025 -
Interpol Arrests Over 300 for Cyber Crimes in Africa
Interpol Arrests Over 300 for Cyber Crimes in Africa
4/4/2025