Forensics Summary for Week of February 9, 2018
By Kimberly Matsumoto on February 9, 2018
Stealthy Magnetic Fields Able to Exfiltrate Data Through Faraday Cages
Malware Name: MAGNETO (PoC) and ODINI (PoC)
Researchers at Ben-Gurion of the Negev Cyber Security Research Center in Israel have published a report showing that magnetic fields can be used to exfiltrate data from an air-gapped computer containing certain malware. They developed two proof-of-concept (PoC) malware designed to regulate the workloads of the CPU on the systems in order to control the magnetic fields being emanated. With this, they can capture and send small pieces of data, such as passwords, encryption keys, or keylogging data, to a nearby receiver. This can be done even if the device is in a Faraday cage, a container designed to to block any inbound and outbound wireless communication, or if the device is in airplane mode.
Air-gapped systems are secured networks where defensive measures are in place to create and maintain a physical separation from public networks. Malicious actors seek to exfiltrate data from these secure networks using what are known as covert channels. For the scenario described here, both the air-gapped computer and the receiver need to be running the malware for the covert channel to function.
Both of the malwares, MAGNETO and ODINI, have the same premise and mode of execution. They take advantage of the basic function of hardware found in almost all modern computers and smartphones: the CPU on a computer which is used for transmission and the magnetometer used for reception of data. The magnetometer, found in smartphones and tablets, typically contains three magnetic sensors that are used to detect the orientation and position of the device. It is not considered a communication interface and thus can be accessed with basic permissions and also remains active even if the device is in airplane mode.
How it works:
Once the malware has been installed on the systems, it starts collecting the data by generating magnetic fields at the required frequency. Magnetic fields are created when current moves through a wire changes according to its acceleration. Modern CPUs are energy efficient which means that there are dynamic changes in its power usage when there is a workload. The malware ends up regulating the workload of the CPU which controls the magnetic field being generated. A way it can do this is by overloading the CPU with calculations, causing it to use a greater amount of power and generating a stronger magnetic field. The malware modulates binary data by intentionally starting and stopping the workload.
The researchers used two modulation schemes for this on-off keying (OOK) and binary frequency-shift keying (B-FSK). In OOK, the data is represented through the presence, “1”, or absence, “0”, of the signal.
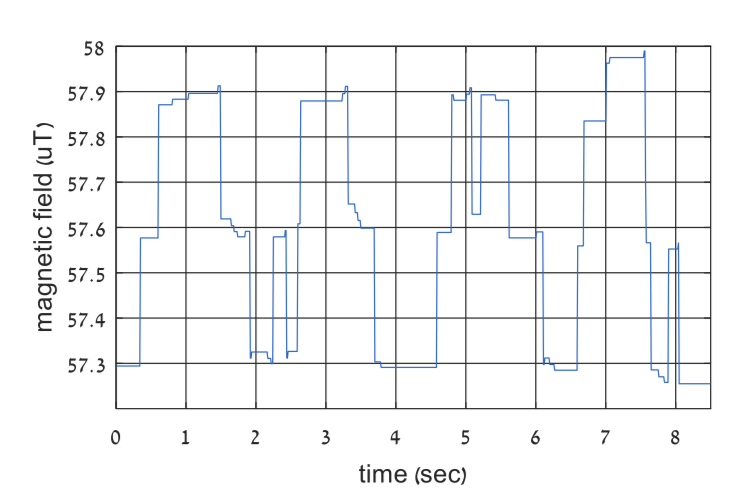
In the B-FSK method, a specific frequency is set to transmit the “1” bits and another is set for the “0” bits.
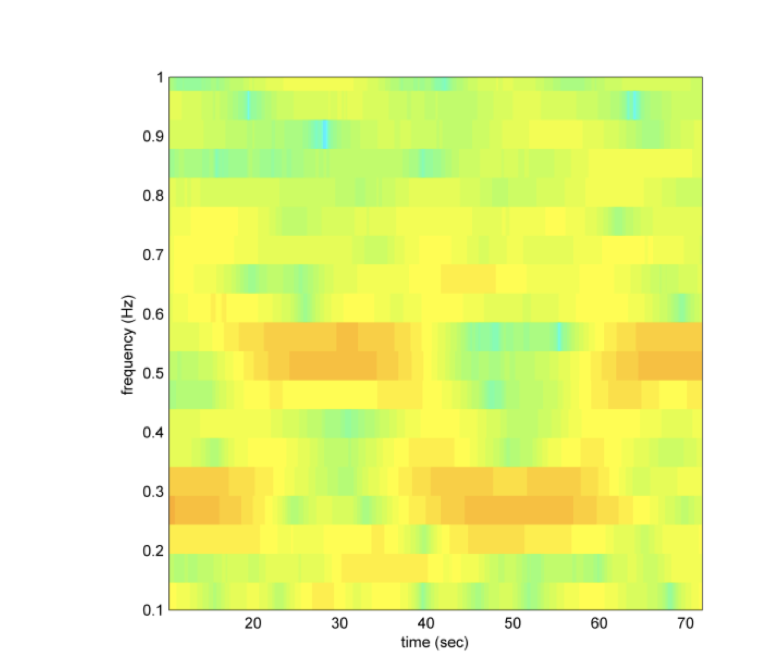
The receiver, in the case of MAGNETO, is a smartphone that has also been compromised with the malware. The researchers used an Android application that accessed the magnetic sensor through the android.hardware.Sensor class and creating an instance of Sensor.TYPE_MAGNETIC_FIELD. The malware uses SensorManager.SENSOR_DELAY_FASTEST setting to sample the magnetic field. Then the SensorSample() event header is invoked whenever new data is sent to the sensor. It has three states of operation which are SAMPLE, PREAMBLE, and DEMODULATE. During SAMPLE it measures the magnetic field, in PREAMBLE it uses the bit-frame header to find the beginning of the frame, and finally during DEMODULATE the signal is extracted.
Video Demonstrations of the Malware
The researchers provided two videos showing the attacks sending data to nearby receivers through Faraday protections.
MAGNETO
ODINI
Differences in the Malware
The two malware developed by the researchers, dubbed MAGNETO and ODINI, have the same result in the exfiltration of data, but there were a few differences. The MAGNETO malware uses uses a regular smartphone for its receiver while ODINI requires a dedicated magnetic sensor. This means that MAGNETO’s mode of transfer is harder to detect because a smartphone would be less conspicuous. They found that MAGNETO’s working distance and speed was much less when compared to ODINI.
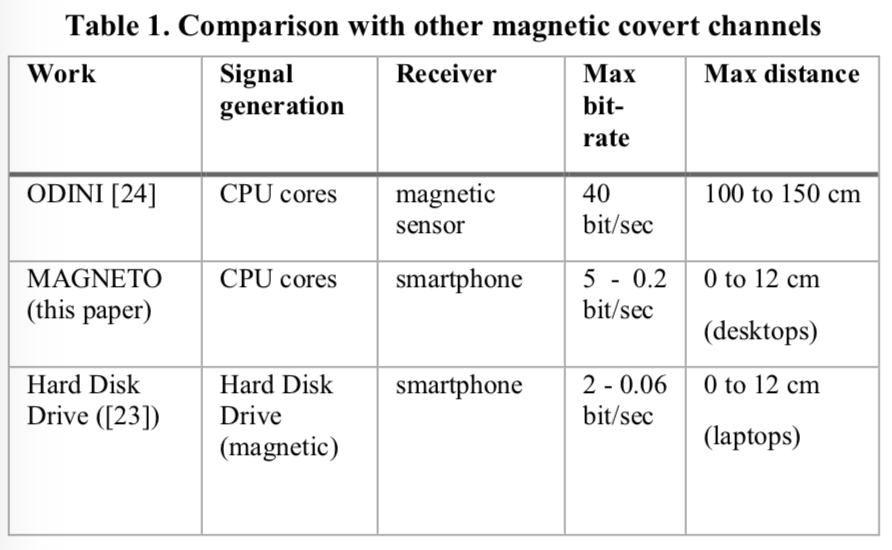
Mitigations
While developed as a proof of concept, this shows the potential threat posed to air-gapped systems. Fortunately, the attacks are dependent on both the air-gapped device and the receiver both being infected so ensuring that good security practices are in place can help to prevent compromise. The researchers recommended some countermeasures to mitigate the issue such as using magnetic shielding, signal jamming, or zoning procedures.
Sources:
MAGNETO: Covert Channel between Air-Gapped Systems and Nearby Smartphones via CPU- Generated Magnetic Fields (Ben-Gurion of the Negev Cyber Security Research Center)
ODINI : Escaping Sensitive Data from Faraday-Caged, Air-Gapped Computers via Magnetic Fields (Ben-Gurion of the Negev Cyber Security Research Center)
New MAGNETO & ODINI Techniques Steal Data From Faraday Cage-Protected Equipment (Bleeping Computer)
Hackers Can Now Steal Data Even From Faraday Cage Air-Gapped Computers (The Hacker News)
Stealthy Data Exfiltration Possible via Magnetic Fields (Security Week)