Spectre and Meltdown: What You Need to Know and How to Protect Yourself
By Jack Giardina on February 2, 2018
What are Spectre and Meltdown?

Earlier this year security researchers made public the discovery of several vulnerabilities affecting nearly every computer, laptop, and smartphone on the market. Known as Spectre and Meltdown, the vulnerabilities exist in the design of modern processors and allow for sensitive information (passwords, e-mail, browsing history) to be read from memory by taking advantage of features known as Speculative Execution and Branch Prediction. The features represent performance enhancing technology that allows processors to pre-execute instructions and predict future execution paths, respectively. It is believed that the Meltdown exploit can be fixed with relative ease, however due to the nature of Speculative Execution we will likely have to settle for mitigation with regards to Spectre. This means that the risk of system compromise will be present for years to come while we wait for a redesign of processor architecture. These flaws have created the potential for exploits that will be undetectable by countermeasures employed by the normal user (antivirus, etc.) and leave no trace in traditional system log files. It is imperative to keep devices updated and carefully monitor vendor announcements as the situation is extremely fluid.
Approximated List of Vulnerable CPUs
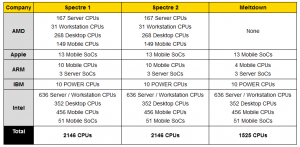
- You can also access the Intel model specific list here.
How They Work:
- Spectre – Breaches the boundaries between different applications and accesses kernel memory, allowing attackers to force secure programs (that follow best practices) into leaking sensitive information. According to Graz , “the safety checks of said best practices actually increase the attack surface and make applications even more susceptible to Spectre.”
- Meltdown – Breaks isolation between common applications and the operation system allowing attackers to access kernel memory, and read sensitive information such as encryption keys or passwords. While data cannot be modified or deleted, the ramifications remain severe given the highly sensitive nature of what is being exposed.
Current Guidance For Protection:
Due to the unprecedented nature of Spectre and Meltdown, guidance for fixes and system protection has been mixed. It is believed that while Meltdown is easily exploitable, it is also easily patched. Fixing Spectre will mostly likely require a redesign of the architecture for nearly all modern processors. Intel rushed to provide BIOS / firmware updates for many of their processors, which resulted in drastic performance loss and caused spontaneous rebooting to occur in many machines. This led the company to issue a recall of those updates, leading to even more confusion for those seeking to protect themselves. While best practices typically require users to keep their machines as up-to-date as possible, this scenario has proven unique given the current instability of the product vendors. On January 29, 2018, Microsoft issued an emergency out of band update to disable Intel mitigation for Spectre Variant 2 that must be downloaded and applied manually. Below is the most current guidance for protection sorted by vendor.
- Apple releases guidance for speculative execution vulnerabilities in ARM-based and Intel CPUs
- ARM Processor Security Update
- AMD Processor Security
- Intel
- Microsoft
- Nvidia Security Updates
Final Thoughts:
The Spectre and Meltdown vulnerabilities have shaken the computing industry to its core. If you are reading this article and thinking that you are probably unaffected, STOP, the list of affected hardware spans nearly every popular device in use today. This includes but is not limited to all Apple devices, and nearly every Intel processor manufactured within the last five years. As research teams and designers work feverishly to provide fixes and mitigation techniques for these issues, the importance of using and understanding best practices for device security has never been greater. It is also quite possible that had processor engineers followed a more strict protocol of best practices rather than leaning forward in pursuit of speed, that these vulnerabilities would not exist at all. While we have not yet seen a large number of exploits surface, security analysts have indicated that time may be fast approaching. Secure your machine as efficiently as possible by practicing defense is depth, and by following the most current guidance available or risk compromise. Do not let yourself be counted as low hanging fruit.
Sources:
Google, https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
Meltdown Attack, https://meltdownattack.com/
Gizmodo, https://gizmodo.com/what-we-know-so-far-about-meltdown-and-spectre-the-dev-1821759062
TechARP, https://www.techarp.com/guides/complete-meltdown-spectre-cpu-list/
Bleeping Computer, https://www.bleepingcomputer.com/news/security/we-may-soon-see-malware-leveraging-the-meltdown-and-spectre-vulnerabilities/