Weekly Executive Summary for Week November 17, 2017
By Joseph Lorenz on November 27, 2017
Monitoring Phase:
Socket: Python library used for Low-level networking interfaces. The socket library is used to open a raw socket and sniff network traffic on the network. Once network packets and headers are captured, struct, another python library is used to format and interpret the byte code that TCP and UDP packets are stored as.
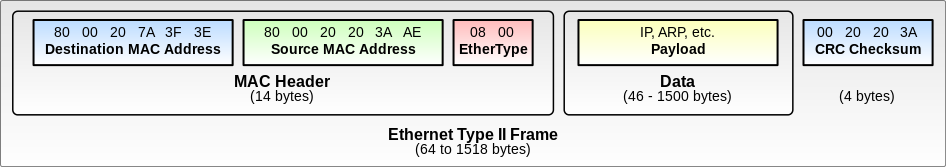
Ethernet packets are captured and data from the packet is extracted using formatting and struct. As you can see below, IP data and header information are contained in the DATA(Payload) section of the Ethernet frame. In this application IP information from the Ethernet packet is essential for creating network rules in other modules.
Source: Wikipedia
Once the Data section from the Ethernet packet is extracted we need to get data from the IP packet header. As seen by the image below, the IP packet contains version, header length, source IP address, destination IP address, and more. The ORB application will only be using the source/destination address for monitoring, once a trusted device is added to the list all incoming network traffic to that device is monitored.
Source: EDGIS
[cc lang=”python” width=”100%” tab_size=”4″]
import socket
import struct
”’IP address of philips hue IoT device”’
ip_mon = ‘192.168.18.162’
[/cc]
Socket and Struct libraries are imported and IP address of philips hue device is stored as a variable to monitor
[cc lang=”python” width=”100%” tab_size=”4″]
”’Creates an open raw socket to capture all network packets”’
conn = socket.socket(socket.AF_PACKET, socket.SOCK_RAW, socket.ntohs(3))
[/cc]
A raw socket object is created to capture network traffic and act as a packet sniffer
[cc lang=”python” width=”100%” tab_size=”4″]
while True:
raw_data, addr = conn.recvfrom(65536)
dest_mac, src_mac, eth_proto, data = ethernet_frame(raw_data)
[/cc]
An endless loop is created to constantly receive data from packets and extract packet data from ethernet frame
[cc lang=”python” width=”100%” tab_size=”4″]
if eth_proto == 8:
(version, header_length, ttl, proto, src, target, data) = ipv4_packet(data)
[/cc]
If the ethernet protocol is equal to ‘8’ it is a IPv4 packet and a function is called to extract packet header information
[cc lang=”python” width=”100%” tab_size=”4″]
if(src == ip_mon):
print(target + ‘:is trying to establish a connection, do you want to accept connections?’)
break
[/cc]
The code will then check if the src address in sniffed packets is equal to the IPv4 address of the IoT device being monitored
To test connections to monitored devices I wrote a python script using a python library called phue. Phue is a python library designed for Philips Hue smart lighting systems, it allows you to connect to a Philips Hue bridge and control lights on a lighting system.
[cc lang=”python” width=”100%” tab_size=”4″]
from phue import Bridge
”’IP address of philips hue bridge”’
b = Bridge(‘192.168.18.162′)
”’Used to connect to the hue bridge – button may need to pressed”’
b.connect()
”’Get the bridge state (This returns the full dictionary that you can explore)”’
b.get_api()
[/cc]
The phue library is imported and a connection is made to the philips hue lighting system bridge and information is returned
[cc lang=”python” width=”100%” tab_size=”4″]
”’Prints if light 1 is on or not”’
b.get_light(1, ‘on’)
”’Set brightness of lamp 1 to max”’
b.set_light(1, ‘bri’, 254)
”’Turn lamp 1 on”’
b.set_light(1,’on’, True)
[/cc]
Hue light information is obtained from the first light in the system and the brightness and power are set to on.
[cc lang=”text” width=”100%” tab_size=”4″]
– IPv4 Packet: – IPv4 Packet: – Version: 4, Header Length: 20, TTL: 64, – Source: 192.168.18.177, Target: 192.168.18.162
– IPv4 Packet: – Version: 4, Header Length: 20, TTL: 64, – Source: 192.168.18.162, Target: 192.168.18.177
– IPv4 Packet: – Version: 4, Header Length: 20, TTL: 64, – Protocol: 6, Source: 192.168.18.177, Target: 192.168.18.162
– IPv4 Packet: – Version: 4, Header Length: 20, TTL: 64, – Source: 192.168.18.177, Target: 192.168.18.162
[/cc]
IPv4 packets are captured and we can see that the Target is the philips hue device as commands are sent to the lights on the hue bridge
Once devices are added to a trusted list from the scanning phase packets in network traffic will be examined, any network traffic to the devices will be captured, and users will be alerted through the application. At this point, users can choose whether they want to traffic from trusted sources or block traffic from untrusted or unrecognized sources.