ICS Summary for Week of October 27, 2017
By Kimberly Matsumoto on October 27, 2017
Critical Vulnerabilities Found in SATCOM Systems
Researchers at IOActive have found two critical vulnerabilities in the AmosConnect 8 SATCOM systems. Created by telecommunications company, Inmarsat, the AmosConnect 8 system provides access to e-mail, instant messages, position reporting, crew internet, automatic file transfer, and application integration in a maritime environment. It’s meant to minimize satellite connectivity costs by optimizing the compression of the data being transmitted.
The first of the critical vulnerabilities they found was a Blind SQL Injection in the login form. A Blind SQL Injection is similar to a SQL injection but differs in that is does not require an error message returned from the server. It instead relies on asking true or false queries to the database.
According to IOActive researchers, this vulnerability in AmosConnect 8 could allow an unauthenticated attacker to acquire stored credentials. These credentials are stored in plaintext on the server of usernames and passwords.
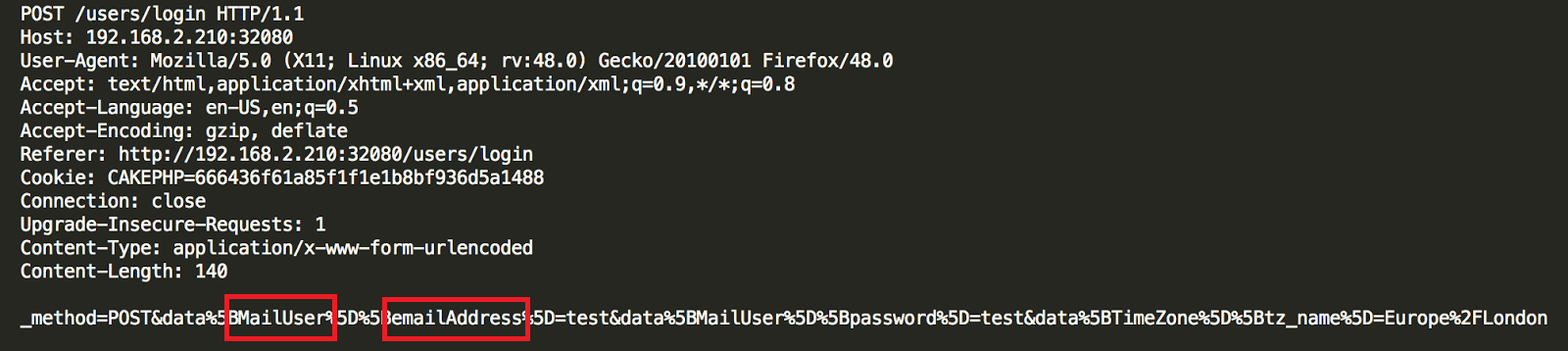
A user logging into the AmosConnect would receive a POST request. It it, the user would see the parameters MailUser and emailAddress. These are the parameters that can be exploited in a Blind SQL Injection that would allow an attacker to gain access to the backend SQLite database. The log in credentials can then be taken by the attacker using the queries:
SELECT key, value from MOBILE_PROPS WHERE key LIKE ‘USER.%.password’;
SELECT key, value from MOBILE_PROPS WHERE key LIKE
‘USER.%.email_address’;
The findByEmail() function in the mail_user.php created a COM object that invokes native C++ coding. In this, the Neptune::ConfigManager::findAllBy() function in this instance allows for the insecure concatenation of the queries. This allows the attacker to perform a SQL query to retrieve data from the database.
The second vulnerability found was a Privileged Backdoor Account vulnerability. The AmosConnect 8 server had a full privileged built-in backdoor account. Through the AmosConnect Task Manager, an attacker could execute high level commands remotely. First, on the login page the Post Office ID was plainly shown.
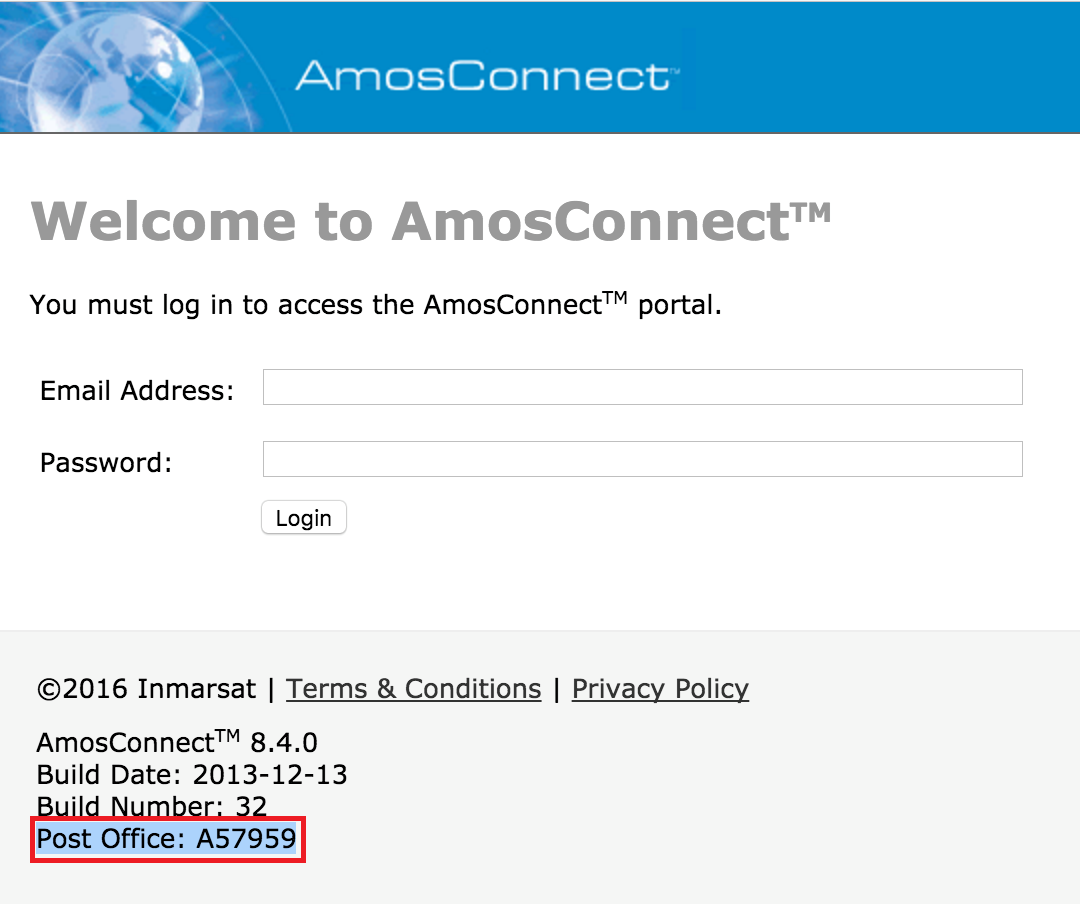
In the authentication method of the mail_user.php, the researchers found a function called authenticateBackdoorUser(). When they looked closer into this, they found that the an attacker could gain the SysAdmin password through use of the Post Office ID.
IOActive notes that most networks on vessels are segmented and isolated, typically into the following segments:
- Navigation Systems Network
- Industrial Control Systems Network
- IT Systems Network
- Bring Your Own Device Network
- SATCOM Network
The vulnerabilities the researchers found could only be exploited through access to the IT Systems Network. They did note that not all vessels have the same segmentation on their networks and that the AmosConnect 8 might have exposure to other areas. This would allow an attacker to gain access to other areas of the network. The researchers warned that “These vulnerabilities pose a serious security risk. Attackers might be able to obtain corporate data, take over the server to mount further attacks, or pivot within the vessel networks.”
Inmarsat has discontinued the AmosConnect 8 as of June 2017. The company has stated that they released a patch to the AmosConnect 8, despite it reaching its end of life, that greatly reduces the risks of exploitation. Their public website also no longer allows users to download or activate the product. Inmarsat also released a statement saying that “this vulnerability would have been very difficult to exploit as it would require direct access to the shipboard PC that ran the AC8 email client. This could only be done by direct physical access to the PC, which would require an intruder to gain access to the ship and then to the computer. While remote access was deemed to be a remote possibility as this would have been blocked by Inmarsat’s shoreside firewalls.”
Sources: AmosConnect: Maritime Communications Security Has Its Flaws (IOActive), Two Critical Vulnerabilities Found in Inmarsat’s SATCOM Systems (Threat Post), Critical flaw in martime comms system could endanger entire ships (HelpNetSecurity)
Note: The purpose of the weekly executive summary is to provide useful information that a business or agency could use in both its cybersecurity and business strategies. In order for this website to serve the community we need to know your concerns and questions about (for example) proper safeguards for technology you’re looking into or what sets of compliance and governance policies would you need to operate a particular business. The CSCC openly invites you to send in your inquiries. We’ll have students research your issues and provide an analysis of the information at hand to guide you with all things cybersecurity. Mail us at: uhwocscc@hawaii.edu
-
New Cybersecurity Regulations Pose Major Shifts for ICS Operators
New Cybersecurity Regulations Pose Major Shifts for ICS Operators
4/4/2025 -
New Threats in Familiar Code: Open-Source Risks in ICS
New Threats in Familiar Code: Open-Source Risks in ICS
4/4/2025 -
The MOVEit Data Breach: Understanding the Risks and Mitigation Strategies
The MOVEit Data Breach: Understanding the Risks and Mitigation Strategies
3/14/2025