Taking advantage of the 4-way handshake
By Joseph Lorenz on October 20, 2017
What is the 4-way handshake?
The 4-way handshake is an amendment to the original 802.11 standard to address security problems in WEP, which was implemented as Wi-Fi Protected Access II (WPA2). Method designed so that an access point (AP) or authenticator, and a wireless client or supplicant can individually prove that each other know the PSK or PMK without ever sending the key.
Terms and definitions:
TK – Temporal Key = session “encryption” key
KCK – Key Confirmation Key = session “authentication” key
KEK – Key Encryption Key = session key for encryption keys
4-Way Handshake – 802.11i key management protocol
AP – Access Point (Authenticator)
STA – STAtion – Client (Supplicant)
GTK – Group Temporal Key
ACK – ACKnowledgement
MIC – Message Integrity Code
PTK – Pairwise Transient Key
PSK – Pre-Shared-Key
Inputs for key encryption:
ANonce – Authenticator Number used once
Nonce – Number used once
PMK – Pairwise Master Key = session authorization token
SNonce – Supplicant Number used once
AA – Authenticator Address – MAC Address
SA – Supplicant Address – MAC Address
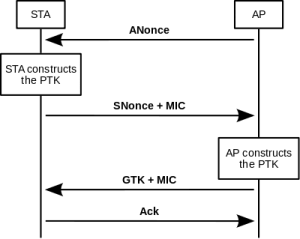
Source: Kali Tutorials
How messages are sent:
- The Access Point (AP) or the authenticator sends a Authenticator Number used once (ANOnce) to the Client. At this point the STAtion (STA) or the client in this case, has all of the inputs required for the construction of Pairwise Transient Key (PTK) for Unicast encryption keys that will be used in the session.
- The STA constructs the PTK and sends its own SNonce to the AP and protects the frame with a Message Integrity Code (MIC) and AP can now calculate the PTK.
- The AP constructs and sends the Group Temporal Key (GTK) and a sequence number. A MIC is used to protect this frame and to prevent tampering of the frame.
- The STA sends a confirmation to the AP to let it know it is ready for encryption.
The PMK is never transferred across the wireless medium
Brute-force attack against 4-way Handshake:
Aircrack-ng is a complete suite of tools used to assess WiFi network security and will be used to monitor/capture the 4-way handshake and eventually crack the WPA Pre-Shared-Key (PSK).
First Step (Monitoring):
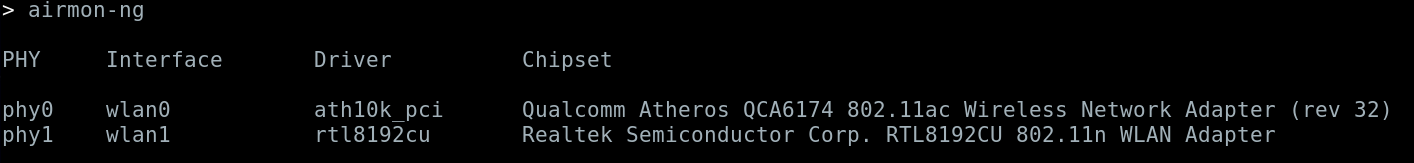
Airmon-ng is a tool in the aircrack-ng suite that allows you to enable a monitoring mode on a wireless interface. It is best when using this tool to stop network managers and kill interfering processes, this feature is built into the tool and a user will be prompted when running it.
Step Two (Capture Packets):
Airdump-ng is another tool in the aircrack-ng suite that can be used to capture 802.11 frames, this is used to capture the 4-way handshake eventually. Capturing the handshake is essential for the eventual cracking.
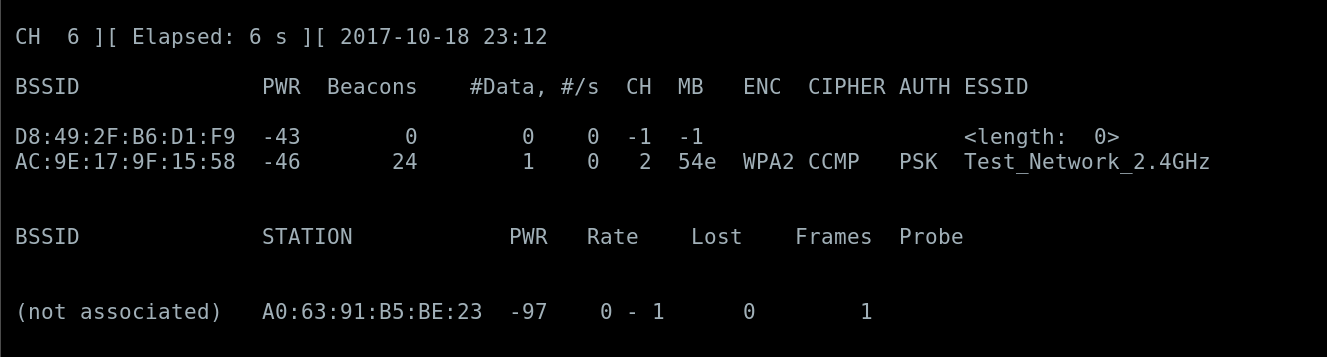
Running airdump-ng allows you to capture a devices Basic Service Set Identifier (BSSID) or the media access control address (MAC Address), the channel the device is broadcasting on, what type of encryption is used (WPA2 in this case), the Extended Service Set IDentification (ESSID) of the network or simply the Service Set IDentifier (SSID).
Step Three (Capture 4-way Handshake):
Users or a single user needs to be bumped of the network so when they reauthenticate the 4-way handshake can be captured. Aireplay-ng is a tool that can be used to deauthenticate users or a single user on the network by jamming the signal. In the example below the deauthentication count is set to 2 and the “-a” or access point is set to the BSSID of the AP.

After a user has been successfully deauthenticated from the network, airdump-ng is used to capture the packets that have the 4-way handshake.
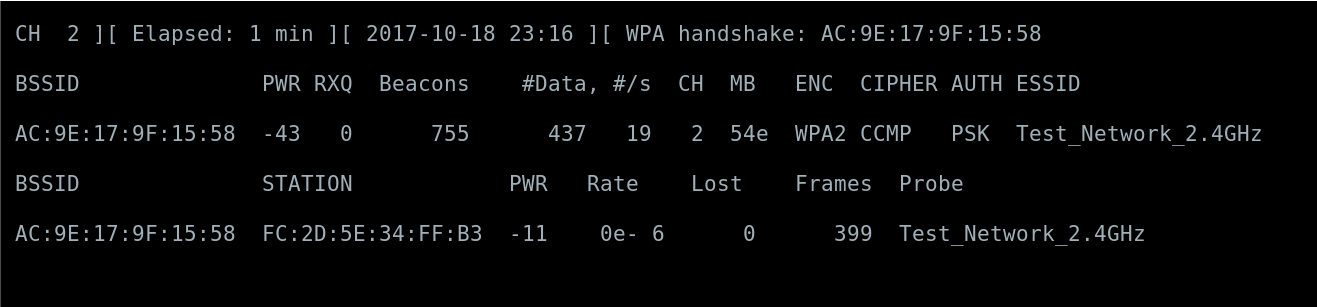
Now that we have obtained the packet captures and the WPA handshake from the reauthentication of a registered user.
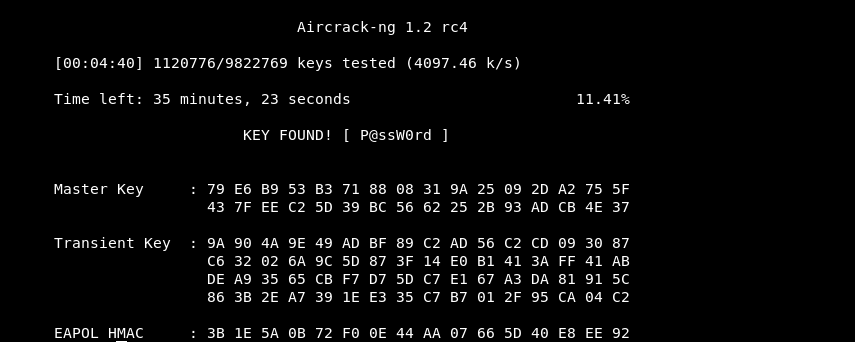
PRO:
- Stealthier than a technique like phishing and attacks can be carried out offline.
- A brute-force attack tends can help to raise less suspicion as the attacks can be done after capturing the handshake.
CON:
- Not very reliable – Password needs to be in a list or fairly easily guessed
- Time consuming – This all depends on a system’s resources
Sources:
http://ieee802.org/16/liaison/docs/80211-05_0123r1.pdf (IEEE)
http://www.kalitutorials.net/2014/06/hack-wpa-2-psk-capturing-handshake.html (Kali Tutorials)