Windows DNS Buffer Overflow
By Justin Cobbs on October 20, 2017

The Domain Name System (DNS) is a protocol that every computer uses to makes hard-to-remember Internet Protocol (IP) addresses, like 172.217.5.78, into something easier for a human to remember, like google.com. When you type google.com into your web browser, it goes to a DNS server to be translated to 172.217.5.78, so that your request is redirected to the proper website, as every website has a specific IP address linked to it. Every computer system, including the Windows Operating System (OS), uses this protocol. In a recent study done by researchers at Bishop Fox, a cybersecurity consultation firm for Fortune 1000 companies, discovered a vulnerability in DNS with Windows 8 and 10 OSes that allows remote code to be executed. This was one of around 60 vulnerabilities that Microsoft had patched on October 10 as a part of Patch Tuesday.
Improper DNS Handling
The vulnerability that affects Windows 8 and 10 OSes is tracked as CVE-2017-11779: Windows DNSAPI Remote Code Execution Vulnerability. Researchers at Bishop Fox had found that this vulnerability is present with the way a Windows process called DNSAPI.dll handles DNS responses. Most notably, the vulnerability is able to be exploited by an attacker modifying a legitimate NSEC3 a Resource Record (RR), in Domain Name System Security Extensions (DNSSEC) that prevents DNS spoofing attacks by authenticating a denial of existence in invalid IP addresses, to return memory addresses on the target system, commonly referred to as a buffer overflow. According to Bishop Fox, the improper parsing of a function called Nsec3_RecordRead results in an out-of-bounds write. DNSAPI.dll also is used by a DnsCache service running under the common name of svchost.exe as NT AUTHORITYNETWORK SERVICE user.
Modified Packets
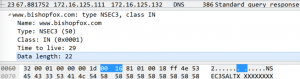
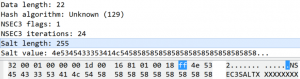
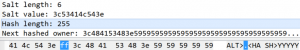
An attacker is able to achieve an out-of-bounds read and write by overflowing three specific heaps. These heaps are within the same packet of the NSEC3 RR and are Data Length, Salt Length, and Hash Length, which results in an Integer Underflow. The data length could be modified to 255 (0xff), which would have 6 (0x6) subtracted to equal 249 (0x00f9). The hash length could be set to 248 (0xf8) and the salt length to 6 (0x6), which when cumulatively subtracted, equals -5 then gets under-flowed to equal 65531. This value is the number of bytes that will be returned from the function memcpy, which could be overwritten to include custom code to redirect to code for a command prompt shell – resulting in allowing arbitrary code execution.
Affected Systems and Patches
Microsoft has released system patches on October 10 to correct the way that DNSAPI.dll handles DNS responses. The systems that are all critically affected by this vulnerability and have patches for it run DNSAPI.dll version 6.3.9600.18512, for Windows 8.1 x86, and version 10.0.14393.206, for Windows 10 x64:
- Windows 10 for 32-bit Systems
- Windows 10 Version 1511 for 32-bit Systems
- Windows 10 Version 1511 for x64-based Systems
- Windows 10 Version 1607 for 32-bit Systems

- Windows 10 Version 1607 for x64-based Systems
- Windows 10 Version 1703 for 32-bit Systems
- Windows 10 Version 1703 for x64-based Systems
- Windows 8.1 for 32-bit systems
- Windows 8.1 for x64-based systems
- Windows RT 8.1
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
Sources
Bishop Fox Analysis:
DNS CVE and Patch:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-11779
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2017-11779
NSEC3 RFC:
https://tools.ietf.org/html/rfc5155#section-3
Windows DNS Articles:
http://www.securityweek.com/hackers-can-execute-code-windows-dns-responses
https://thehackernews.com/2017/10/microsoft-security-patches.html
-
CrushFTP CVE-2025-31161 Vulnerability
CrushFTP CVE-2025-31161 Vulnerability
4/11/2025 -
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
Active Exploitation of Apache Tomcat CVE-2025-24813 Vulnerability
4/4/2025 -
Next.js Middleware CVE-2025-29927 Vulnerability
Next.js Middleware CVE-2025-29927 Vulnerability
4/4/2025