Equifax Megabreach Update: How, who, and more
By MDL on September 15, 2017
Last week, we reported that the major credit reporting company Equifax announced a massive data breach affecting up to 143 million US customers last week on 7 September, but the developing story over the course of the week has gone from bad to worse.
How the Breach Occurred
After days of speculation, on 13 September, Equifax revealed the initial attack vector that unknown hackers exploited to enable the breach, a known Apache Struts web-application vulnerability, CVE-2017-5638. This particular vulnerability was disclosed and patched by 8 March of 2017, months before the start of the breach on 13 May 2017, meaning that this dangerous and widespread data breach was easily preventable.
Continuing Technical Problems
Technical problems have plagued Equifax in the week since the breach was announced. The PIN generated to enable and disable security freezes was found to be easily predictable, incorporating the date and time of the freeze request. The credit freeze request link was temporarily unavailable due to “technical issues” related to the high volume of security freeze requests. The Equifax informational breach website has addressed these problems in updates (2, 3, 4 ) and worked to correct them.
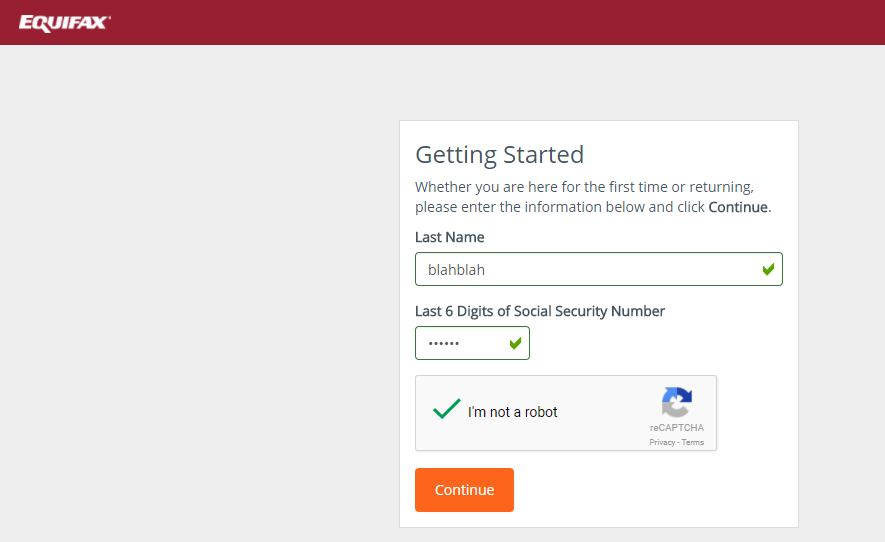
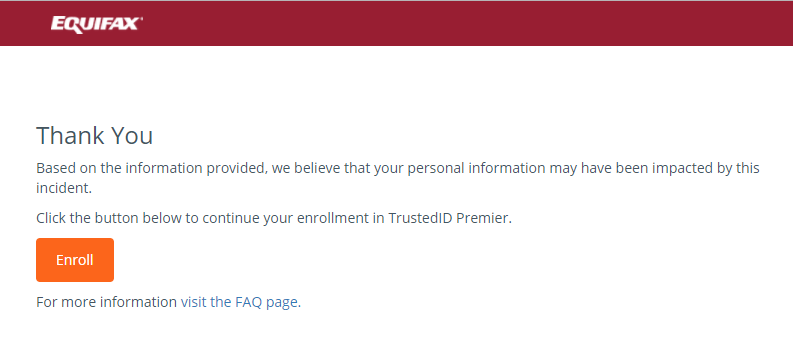
The TrustedID Premiere online checker that allows users to determine whether or not they were affected was widely reported to be unreliable, and these problems seem to persist. As of 15 September, the checker still returned different responses for the same user checking multiple times, and checks for the last names “test” and “blahblah” with the social security number “123456” still returned the result “we believe that your personal information may have been impacted by this incident.”
Security researcher Brian Krebs documented the case of an Equifax Argentina employee online portal used to manage customer credit disputes page was secured by only the username/password combination admin/admin even after the massive data breach had already revealed.
On 15 September, Equifax announced two “personnel changes” upon the immediate retirements of their Chief Information Officer and Chief Security Officer. An interim CIO and CSO have been named while the investigation continues with the help of the FBI.
Update: Who Was Affected
Last week’s Equifax statement announcing the breach stated that 143 million US customers, or 44 percent of the US population, may have been affected, while “some data” from Canadian and UK residents may have been affected.
This week, articles by The Guardian and The Telegraph reported that Equifax holds the data of 44 million UK residents, or 67 percent of the population, which was also illegally accessed during the breach. UK residents were not able to use Equifax’s online checker to determine if they had been affected because it required users to enter a US Social Security Number. Equifax UK later clarified on their informational incident webpage that “fewer than 400,000 UK consumers” will be contacted that their data may have been illegally accessed in the breach. The Equifax UK statement says that “due to a process failure,” some UK customer data was stored in the US from 2011 to 2016, but that the data accessed was more limited in scope than that of the American customers. “The information was restricted to: Name, date of birth, email address and a telephone number and Equifax can confirm that the data does not include any residential address information, password information or financial data.”
Worryingly, the Guardian article also mentioned an Equifax marketing document written for a UK audience that boasts of the company holding “over 10 million child data records, to provide insights to a household.” Equifax has not provided any statements on its informational website or the UK webpage dedicated to the breach about child records being accessed. If fact, no mention of child data records can be found on either websites at all.
Congressional Hearings
This week, two US Congressional panels, the House Financial Services Committee and the House Energy and Commerce Committee, announced that they planned to hold hearings on the Equifax data breach. Equifax CEO Richard Smith has already received a formal letter of request to testify at the House Energy and Commerce Committee hearing scheduled form 3 October.
Read our initial CSCC article on the Equifax breach for more background information. For recommendations and links for those who may have been affected, read our CSCC Best Practices article.
Sources:
Equifax, Cybersecurity Incident & Important Consumer Information
Equifax, Updates
Equifax, Equifax Releases Details on Cybersecurity Incident, Announces Personnel Changes
Equifax, Trusted ID Premiere, Eligibility
Equifax, Equifax Household Composition (pdf)
Equifax UK, Cybersecurity incident – UK update
NIST, National Vulnerabilities Database, CVE-2017-5638 Detail
Krebs on Security, Ayuda! (Help!) Equifax Has My Data!
Wired, EQUIFAX OFFICIALLY HAS NO EXCUSE
The Guardian, Equifax told to inform Britons whether they are at risk after data breach
The Telegraph, Equifax hack: 44 million Britons’ personal details feared stolen in major US data breach
Recode, The U.S. Congress is going to hold two hearings on the massive Equifax data breach
The Hill, Equifax CEO formally called to testify before Congress
-
Denmark Faces Largest Cybersecurity Incident to Date
Denmark Faces Largest Cybersecurity Incident to Date
12/8/2023 -
Defense Contractor, Japan Aviation Electronics, Falls Victim to a Cyber Attack
Defense Contractor, Japan Aviation Electronics, Falls Victim to a Cyber Attack
12/8/2023 -
North Korea Infiltrates Remote US Jobs to Fund Weapons
North Korea Infiltrates Remote US Jobs to Fund Weapons
11/2/2023