Weekly Executive Summary for Week August 18, 2017
By Joseph Lorenz on August 17, 2017
What is it? Android Spyware
What has it been dubbed? SonicSpy | Soniac
What does it do?
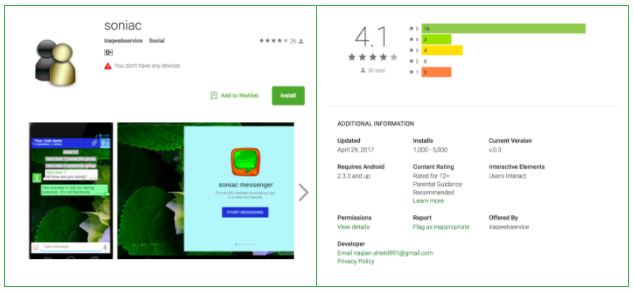
The spyware was discovered in an application called Soniac, it was being distributed through the Google Play Store as a messaging app. There were also two other apps called Hulk Messenger and Troy Chat, that were being distributed in the Google Play Store with the same spyware capabilities. The Android spyware has the ability to record audio, take photos with the camera, make outbound calls, send text messages to attacker specified numbers, retrieve information from the device, and send the collected data to a Command and Control server (setup by attackers). Soniac provided functionality of a popular messaging app Telegram(which is the most widely used messaging app in Iran), while also executing its nefarious commands in the background.
According to researchers at Lookout, the developers of the SonicSpy spyware family were most likely based in Iraq. The domain infrastructure has references to the country and the name of the developer account was iraqwebservice. The term “Iraqian Shield” appears constantly in code of these malicious apps.
How does it do it?
Samples of the SonicSpy family have been identified by researchers since February 2017, and a number of these malicious apps were being distributed through the official Google Play Store. The first malicious app that was found in the Play Store was Soniac, an application that does provide the functionality of Telegram messaging app and contains other spyware capabilities.
Source: Lookout
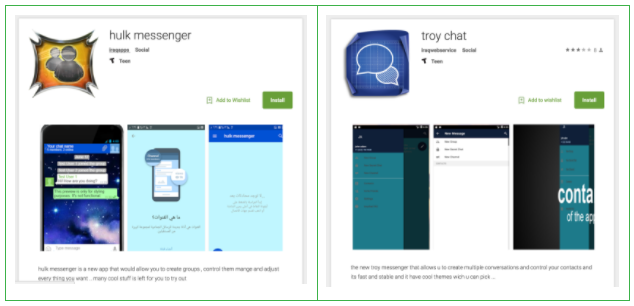
Two other malicious apps were found on the Play Store Hulk Messenger and Troy Chat, both of them were removed fairly quickly, but it is unclear if it was Google or the threat actors who removed the applications. Soniac was removed from the Play Store by Google after being alerted of the malicious application by researchers from Lookout.
Source: Lookout
Upon execution SonicSpy will remove its launcher icon to hide itself from a victim, it then proceeds to connect to a C2(Command and Control) server “arshad93.ddns[.]net:2222”. At this point, SonicSpy will install its own custom version of Telegram that is stored in “res.raw” directory and is named “su.apk”.
Researchers at Lookout were able to identify what type of traffic has been sent from infected devices by running netcat on port 2222.
Source: Lookout
The SonicSpy spyware family has the ability to use 73 remote instructions. The Soniac application included some of these commands such as silently recording audio, taking photos with the camera, making outgoing calls, sending text messages to any specified number, and retrieving information like call logs, contacts, and Wi-Fi access points.
Conclusion:
Recently, Google has released its new security system called Google Play Protect, which uses (AI) Artificial Intelligence to scan apps on devices daily to monitor for malicious behaviors. I posted an article a few weeks ago that described how the service was able to detect malicious apps that were being distributed through the Play Store, but it seems that similar malicious apps with spyware capabilities are still being identified in the store.
It seems that a number of spyware families have been discovered targeting Android devices, these include Lipizzan, SonicSpy, Jingwang app, and more. Many of the malicious apps found containing these spyware are being disguised as messaging applications, as they are very popular amongst everyday users as well as government officials. This can be very dangerous as spyware allows attackers to gain useful information before it can be properly encrypted by messaging apps like Whatsapp, Telegram, etc.
This is another great example of how not only should users make sure apps are installed from the official Google Play Store, but they should also look at user reviews, number of user installs, and be aware of what types of permissions the newly downloaded app is asking for. Their have been numerous cases of malicious applications being distributed through the Play Store, so users should be alert when installing new applications.
Sources:
https://arstechnica.com/information-technology/2017/08/android-users-bombarded-with-4000-spy-apps-three-land-in-google-play/ (Ars Technica)
https://blog.lookout.com/sonicspy-spyware-threat-technical-research (Lookout)
https://threatpost.com/apps-infected-with-sonicspy-spyware-removed-from-google-play/127406/ (Threatpost)
-
Smart/IoT Devices as Evidence Sources
Smart/IoT Devices as Evidence Sources
4/16/2024 -
Applications and Challenges of Artificial Intelligence for Digital Forensics
Applications and Challenges of Artificial Intelligence for Digital Forensics
4/16/2024 -
Challenges in Digital Forensics for the Internet of Things
Challenges in Digital Forensics for the Internet of Things
3/28/2024